The latest Discord data breach has raised serious questions about the safety and transparency of one of the world’s most widely used communication platforms. On September 20, Discord disclosed that attackers gained unauthorized access to a third-party customer service system used by the company. As a result, sensitive user information was exposed, including names, Discord usernames, email addresses, IP addresses, partial payment details, and even the content of support messages and attachments. While Discord emphasized that passwords and full credit card numbers were not stolen, the data revealed in its own notifications shows that users face serious risks such as phishing, fraud, harassment, and identity theft.
Compounding the problem is Discord’s delayed and inconsistent response. Some users received notification emails within days, others including the author of this report did not receive any alert until October 3, nearly two weeks after the breach. Many users who previously interacted with Discord support report not being contacted at all. This staggered approach has left a large portion of the community vulnerable during the critical early period when exposed data is most likely to be exploited. The slow and uneven response has sparked backlash and renewed criticism of Discord’s history of poor communication, weak oversight, and failure to adequately protect its users.
This article provides the full notification email sent to affected users, breaks down exactly what information was exposed and what was not, analyzes why this breach matters for millions of users, and gives practical steps to secure your accounts. It also examines Discord’s reliance on third-party vendors, the risks this creates, and what lessons users and companies should take away from this incident.
Table of Contents
- Example of Discord’s Email Notice
- What Data Was Exposed
- What Data Was Not Exposed
- Why This Data Breach Matters
- Discord’s Official Response and Timing
- Immediate Steps You Should Take
- Additional Protection and Monitoring
- The Bigger Picture of Third-Party Risk
- Key Takeaways
Example of Discord’s Email Notice
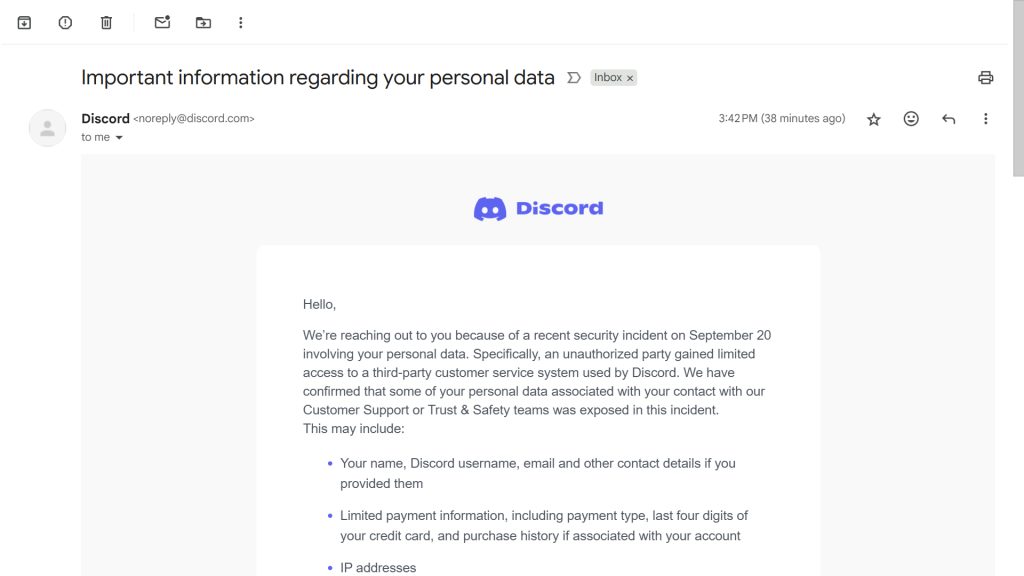
When a data breach happens, the first communication users receive is usually the company’s official email notice. This message sets the tone, outlines what the company admits, and often reveals how transparent or evasive the organization will be. In the case of the Discord data breach, affected users were sent an email with the subject line: “Important information regarding your personal data.” For many people, this was the first and only notice that their personal information had been exposed.
The timing of these emails has also been a major issue. Some users received them within days of the September 20 incident, while others did not receive anything until October 3. Many claim they never received an email at all, despite having interacted with Discord’s support teams. This uneven notification process created confusion and left many users unaware during the most critical period after a breach, when stolen data is most likely to be exploited.
Below is the full text of the email Discord sent to affected users. The only part removed is the unique ticket number, which we have redacted. This reproduction allows readers to see exactly how Discord framed the situation and what details it chose to disclose.
Hello,
We’re reaching out to you because of a recent security incident on September 20 involving your personal data. Specifically, an unauthorized party gained limited access to a third-party customer service system used by Discord. We have confirmed that some of your personal data associated with your contact with our Customer Support or Trust & Safety teams was exposed in this incident.
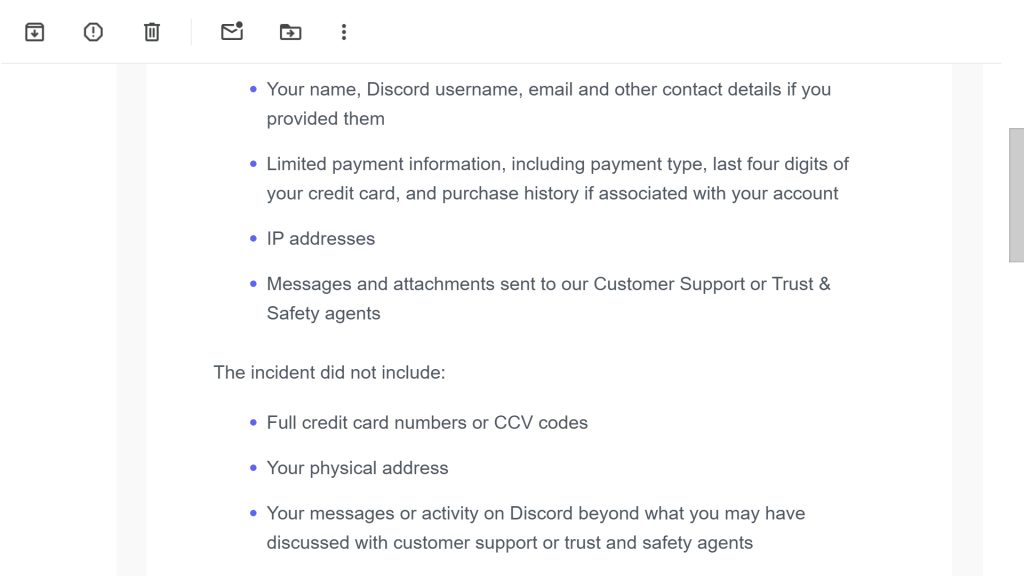
This may include:
- Your name, Discord username, email and other contact details if you provided them
- Limited payment information, including payment type, last four digits of your credit card, and purchase history if associated with your account
- IP addresses
- Messages and attachments sent to our Customer Support or Trust & Safety agents
The incident did not include:
- Full credit card numbers or CCV codes
- Your physical address
- Your messages or activity on Discord beyond what you may have discussed with customer support or trust and safety agents
- Your Discord password or authentication data
The ticket numbers impacted for your account were: [REDACTED]. You can use these ticket numbers to search for the relevant exchanges in your email account.
As soon as we became aware of this incident, we followed our incident response procedures and took immediate steps to address the situation, including revoking the customer support provider’s third-party access to our ticketing system, launching an internal investigation, and engaging a leading forensics IT firm to support our investigation and remediation efforts. We’ve also notified law enforcement of the incident.
Discord has and will continue to take the appropriate steps in response to this situation. We have reviewed our threat detection systems and security controls for third-party support providers at Discord. As standard, we will continue to frequently audit our third-party systems to ensure they meet our high safety standards.
Looking ahead, we recommend that you stay alert when receiving messages or other communication that may seem suspicious. We have service agents on hand to answer questions and provide additional support. You can contact us through this form: http://dis.gd/support
We take our responsibility to protect your personal data seriously and understand the inconvenience and concern this may cause.
This email matters because it represents the only official confirmation many users ever received. The language is intentionally vague, using terms like “limited access” and “this may include” rather than clearly stating what was stolen. The emphasis on what was not exposed also attempts to soften the impact, but it distracts from the fact that sensitive information such as IP addresses, support messages, and partial payment data was accessed. For users, this lack of clarity creates uncertainty and forces them to assume the worst.
In the next section, we will break down what data was exposed in the Discord data breach, explain why each type of information matters, and how attackers can use it against you.
What Data Was Exposed in the Discord Data Breach?
When news of the Discord data breach broke, the biggest concern for users was what information attackers actually gained. Discord’s email to affected users used vague wording such as “this may include,” which leaves uncertainty about exactly what was stolen. Because of this lack of clarity, every person who has ever interacted with Discord’s Customer Support or Trust and Safety teams must assume that their personal details were part of the exposure. Below is a breakdown of the categories of information that may have been compromised and why each one matters.
Exposed Information
- Names, Discord usernames, and email addresses: These identifiers allow criminals to create realistic phishing attacks. For example, an attacker could email you using your real name and Discord username, making a scam message appear authentic and convincing.
- IP addresses: An IP address reveals your approximate location and internet provider. This data can be abused to target victims with scams that appear regional, or even to launch disruptive denial-of-service (DDoS) attacks against gamers and streamers.
- Limited payment information: This includes the last four digits of credit cards, payment type, and purchase history. Although attackers cannot directly process charges with this data, it is useful in social engineering scams. Fraudsters can cite your partial payment details to impersonate you when contacting banks or customer service representatives.
- Support messages and attachments: The most sensitive information exposed came from support tickets. These often include private conversations, screenshots, or uploaded documents. For users who reported harassment, billing issues, or shared identification files, this creates major risks of blackmail, impersonation, or harassment.
Why This Exposure Matters
Even though Discord stated that passwords and full payment details were not taken, the data that was exposed still carries serious risks. Cybercriminals rarely rely on one piece of information. Instead, they combine fragments from different leaks to build complete profiles of victims. An exposed email address and username from this breach, for example, could be matched with a password leaked elsewhere, allowing attackers to compromise accounts across multiple platforms.
The exposure of IP addresses makes phishing more convincing because attackers can tailor scams to your location. For creators and streamers, an IP leak can also enable harassment or DDoS attacks that disrupt live broadcasts. The inclusion of limited payment data makes impersonation more credible, giving scammers a foothold to bypass verification checks. Finally, the loss of support ticket content is especially concerning because it contains context that criminals can exploit to craft highly targeted attacks.
The bottom line is that while Discord emphasized what was not exposed, the information that was potentially accessed is more than enough to put users at risk. This breach highlights the need to treat partial leaks with the same seriousness as complete credential theft, because even fragments of data can be weaponized once they are in the hands of criminals.
Next, we will examine what data was not exposed and why Discord chose to highlight those details in its notification.
What Data Was Not Exposed in the Discord Data Breach?
In its notification email, Discord emphasized not only what information may have been compromised but also what attackers did not gain access to. While these exclusions may sound reassuring at first, they must be looked at critically. Just because certain categories of data were not exposed does not mean users are safe. It is important to understand what was excluded, why Discord chose to highlight these details, and whether that reassurance should be trusted.
Data That Was Not Exposed
- Passwords and authentication data: Discord confirmed that user passwords, password hashes, and two-factor authentication (2FA) codes were not part of the breach. This means attackers cannot directly log into accounts using stolen credentials from this incident.
- Full credit card numbers and CVV codes: While limited payment details such as the last four digits of cards were exposed, complete card numbers and CVV codes were not. This reduces the chance of attackers making direct fraudulent charges with stolen data from this breach alone.
- Physical addresses: Discord’s message stated that no home addresses or physical locations were exposed. However, this reassurance has limits since exposed IP addresses can still reveal approximate geographic areas.
- General Discord messages and server activity: The company clarified that everyday chats, private messages, and community activity were not accessed. The compromise was limited to customer support and Trust and Safety interactions.
Why These Exclusions Matter
On the surface, this information provides some relief. Knowing that passwords and credit card numbers were not stolen means fewer immediate risks of account takeovers or direct fraudulent charges. However, these reassurances should not overshadow the seriousness of what was exposed. Criminals do not always need full financial or login credentials to launch effective attacks. Partial details such as usernames, emails, IP addresses, and support messages can be more valuable for targeted scams.
The Psychology of “Not Exposed”
The order of information in Discord’s notification email matters. By highlighting what was not stolen before explaining what was exposed, the company attempted to frame the incident in a less alarming way. This communication strategy is common after breaches, but it can create a false sense of security for users. Someone skimming the email might walk away thinking the situation is minor because their password and card numbers were not included. In reality, the other data categories are still highly sensitive and useful to attackers.
Why Users Should Remain Cautious
Even with these exclusions, affected users should not relax. Attackers specialize in combining data from different leaks. A Discord username and email address from this breach could be paired with a password from another database. A partial card number could be combined with address details from a separate leak to commit fraud. A support ticket transcript could provide context that makes phishing attempts feel authentic. Each piece of data has value, even if Discord tried to downplay the impact by focusing on what was not exposed.
While the absence of stolen passwords and card numbers is positive, it does not eliminate the risks created by this incident. Users must remain cautious, assume their data could be abused, and take proactive steps to secure their accounts.
Why This Discord Data Breach Matters
When companies suffer security incidents, many people immediately ask the same two questions: were passwords stolen and were credit card numbers compromised? In the case of the Discord data breach, the company emphasized that neither of these categories of information were exposed. While that may sound reassuring, it risks creating a false sense of safety. The reality is that the information that was exposed is more than enough to create serious risks for millions of users. Real names, Discord usernames, email addresses, IP addresses, partial payment details, and even messages and attachments from support tickets all carry significant value to attackers.
Why Partial Data Exposure Is Still Dangerous
One of the biggest mistakes people make after a breach is assuming that partial information is harmless. In practice, cybercriminals rarely need complete credentials to launch an attack. A stolen email address can be used for phishing. A partial credit card number can be used to impersonate a customer with banks or online services. An IP address can be used to geolocate a victim or launch denial-of-service attacks. When these fragments are combined with data from other breaches, they create powerful profiles that enable sophisticated fraud and identity theft.
Examples of How This Data Can Be Used
- Phishing campaigns: Emails that greet you by your Discord username and reference support issues you actually had will appear authentic. These highly targeted scams have a much higher success rate than generic spam.
- Credential stuffing: Even though Discord passwords were not exposed, attackers can use your email address to test old password combinations from previous breaches across multiple platforms, including Discord.
- DDoS attacks: For gamers and streamers who rely on Discord, exposed IP addresses can be used by attackers to flood a connection and knock them offline.
- Fraudulent impersonation: Attackers can use partial payment details, such as the last four digits of your credit card, to impersonate you with customer service or financial institutions.
- Social engineering: Support ticket messages and attachments could contain sensitive personal details. Attackers can exploit this context to craft scams or extortion attempts that feel legitimate.
Impact on User Trust
Discord is not just a chat app for gamers anymore. It has become a platform for businesses, classrooms, nonprofit organizations, and communities that rely on it for communication and collaboration. When sensitive data is exposed, it undermines the trust that makes those communities possible. Users may now feel hesitant to contact customer support, worried that their private conversations and attachments could end up in the wrong hands. For organizations that rely on Discord for sensitive or professional communication, this loss of confidence could have long-term consequences.
Why Delayed Notifications Make It Worse
The seriousness of this breach is compounded by Discord’s delayed communication. The breach occurred on September 20, yet many users did not receive notification emails until October 3. Others report that they have still not been contacted despite having support interactions that could have been exposed. Every day of delay gives attackers more time to abuse stolen data while victims remain unaware. This slow and uneven rollout of notifications suggests that Discord either lacked visibility into the scope of the breach or chose to limit disclosure to protect its reputation.
The Bigger Cybersecurity Picture
This incident is also part of a larger trend in cybersecurity. Attackers are increasingly targeting third-party vendors rather than a company’s core systems. By breaching a support provider that handled Discord’s customer service data, attackers gained access to sensitive information without ever directly compromising Discord’s infrastructure. These supply chain weaknesses are among the most common and devastating vulnerabilities in the modern digital ecosystem. It shows that your data is only as safe as the weakest vendor a company relies on.
Legal and Regulatory Risks
Depending on where affected users live, Discord could face regulatory scrutiny under laws such as the General Data Protection Regulation (GDPR) in Europe or the California Consumer Privacy Act (CCPA) in the United States. Both require timely disclosure of breaches and adequate protection of personal data. If regulators find that Discord failed to secure its vendors or delayed notifications unnecessarily, the company could face significant fines and reputational damage.
Why Users Cannot Ignore This Breach
Even though passwords and full card numbers were not exposed, the Discord data breach still matters because attackers can and will exploit partial information. The combination of email addresses, usernames, IPs, partial payment data, and private support messages is more than enough to enable phishing, fraud, harassment, and identity theft. The delayed and vague response from Discord only makes it worse, leaving many users unprepared and at risk. For these reasons, this breach should be taken seriously by anyone who has ever interacted with Discord’s Customer Support or Trust and Safety teams.
Discord’s Official Response
When evaluating the severity of a security incident, it is not enough to look at what information was exposed. The way a company responds is often just as important. In the case of the Discord data breach, the company’s response has already drawn heavy criticism. While Discord confirmed the incident and sent out notification emails, the timing, wording, and scope of these messages suggest that the company prioritized reputation management over user protection.
Delayed Notifications
The breach occurred on September 20, but many users did not receive emails until October 3, nearly two weeks later. Others report never being contacted at all, despite having past interactions with Discord’s support system. This delay left users in the dark during the most critical period after a breach, when stolen data is most likely to be sold or misused. Every day of silence gave attackers a head start, while victims had no opportunity to take protective steps such as changing credentials, monitoring bank accounts, or scanning for phishing attempts.
Uneven Communication
Notifications were not sent to all potentially affected accounts at the same time. Some users were contacted within a few days, while others received emails weeks later or not at all. This inconsistent rollout suggests that Discord either did not know the full scope of the breach or deliberately chose to limit disclosure. Both possibilities are troubling. A company of Discord’s size should be able to determine whose data was compromised quickly and notify all victims without delay.
Vague and Minimizing Language
Discord’s email repeatedly used vague phrases such as “limited access” and “this may include”. Instead of clearly confirming what data was stolen, the company left users guessing. This lack of transparency shifts the burden onto users, who must assume that everything listed was exposed. The email also dedicated significant space to emphasizing what was not exposed, such as passwords and full credit card numbers, before fully explaining what information was compromised. This is a public relations tactic designed to reduce panic, but it risks misleading users into believing the breach was minor.
Comparison to Best Practices
Industry best practices for breach notification, such as those outlined in GDPR and CCPA regulations, call for clear, prompt, and transparent disclosure. Companies are expected to notify affected users “without undue delay” and to provide specific details about what was accessed, how it happened, and what steps users should take. By these standards, Discord fell short. The two-week delay, the vague descriptions, and the lack of actionable guidance show that the company’s response did not meet regulatory or ethical expectations.
A Pattern of Weak Oversight
The poor handling of the Discord data breach mirrors other long-standing issues with the platform. Discord has often been criticized for being slow to address reports of predators, harassment, and harmful communities. Many users see this breach as another example of the company reacting slowly and prioritizing public image over user safety. By outsourcing critical support functions to a third-party vendor and then failing to communicate promptly when that vendor was compromised, Discord demonstrated a pattern of weak oversight that extends beyond moderation to cybersecurity itself.
Community Backlash
The response triggered frustration across Discord’s user base. Many users reported that they only learned about the breach from news outlets, community forums, or suspicious activity in their accounts rather than from Discord directly. Others expressed anger at the inconsistent notifications, viewing them as evidence that the company cared more about damage control than protecting its users. For a platform that markets itself as a place for real-time communication, the slow and uneven response felt especially ironic and disappointing.
Why This Response Matters
A company’s response to a data breach often determines whether users can quickly defend themselves. In this case, Discord’s delayed notifications, vague language, and focus on minimizing panic left users unprepared. Instead of empowering people to act, the company’s communication strategy downplayed the risks. For many users, this is more damaging than the breach itself. The lack of urgency and transparency has eroded trust, raising doubts about whether Discord will be honest and proactive if future incidents occur.
Steps Users Should Take Now
After a major incident like the Discord data breach, the most urgent question is simple: what should you do right now to protect yourself? Discord’s notification email only suggested that users “stay alert,” which is far too vague. In reality, the exposure of names, emails, IP addresses, partial payment information, and support messages requires immediate and specific action. The steps below will help you secure your accounts, reduce your risk of fraud, and regain control over your personal data.
1. Change Your Discord Password and Enable 2FA
Although Discord stated that passwords were not included in the breach, you should act as if they were at risk. Hackers often combine data from different leaks. If your email or username is tied to an old breach where your password was exposed, your Discord account could be targeted through credential stuffing.
- Create a new, strong password that is unique to Discord.
- Do not reuse passwords from other services.
- Enable two-factor authentication (2FA) to add a critical layer of protection.
- Check active sessions in your account and log out of devices you do not recognize.
2. Secure Your Email Account
Your email address was one of the most sensitive details exposed in the Discord data breach. If attackers gain access to your inbox, they can reset passwords and compromise multiple accounts.
- Change your email password immediately and make it unique.
- Enable 2FA on your email account to prevent unauthorized access.
- Review your email login history for suspicious activity.
- Consider using a secondary email for important accounts like banking or work.
3. Monitor Bank and Payment Accounts
Discord admitted that limited payment details, such as card type and the last four digits, were exposed. While attackers cannot directly charge your card with this information, they can use it to impersonate you or build credibility in scams.
- Check your bank and credit card statements regularly for unauthorized activity.
- Contact your bank to ask if replacing your card is necessary.
- Set up transaction alerts so you receive notifications of every purchase.
- Watch for unusual small charges, which may be test transactions by criminals.
4. Refresh Your IP Address and Protect Your Network
The exposure of IP addresses in the Discord data breach creates risks such as phishing attempts, harassment, or even denial-of-service attacks.
- Restart your modem and router to obtain a new IP address from your provider.
- Use a VPN to hide your IP and encrypt your traffic.
- Disable remote access features on your router unless you need them.
- Update router firmware to close known vulnerabilities.
5. Review Your Past Discord Support Tickets
One of the most serious parts of this breach is that support messages and attachments may have been exposed. These can include screenshots, financial details, or sensitive conversations.
- Look through your past tickets to see what information you may have shared.
- If you uploaded financial or ID documents, contact your bank or local agency for advice on replacement or monitoring options.
- If the tickets involved harassment or personal disputes, be alert for possible extortion attempts.
- Do not respond to threats or extortion. Report them to Discord and law enforcement.
6. Scan Your Devices for Malware
Breached data is often used to create phishing messages that deliver malware. Running a scan ensures your system is not already compromised.
- Download and install a trusted anti-malware tool such as Malwarebytes.
- Run a full system scan and remove any threats.
- Enable real-time protection to guard against future infections.
7. Be on High Alert for Phishing Attempts
With your email, username, and partial details exposed, scammers may try to impersonate Discord or your bank.
- Do not click links in unsolicited emails claiming to be from Discord.
- Verify suspicious messages by going directly to discord.com.
- Be cautious of emails that reference Nitro subscriptions or support tickets.
- Never share passwords, 2FA codes, or payment details via email.
8. Consider Credit and Identity Protection
Since partial payment information and personal identifiers were involved, enrolling in an identity protection service may be worthwhile. These services can monitor for suspicious activity and alert you if your data appears in new leaks.
Why Taking Action Matters
The Discord data breach is not just an isolated event. Criminals often combine data from multiple leaks to create detailed profiles of victims. Even if Discord passwords and full card numbers were not exposed, the fragments stolen in this incident can still be used for fraud, phishing, and harassment. Acting quickly is the best way to minimize your risks and protect your digital identity.
Additional Protection Tips
Taking immediate action after the Discord data breach is essential, but long-term protection is just as important. Cybercriminals often store and reuse stolen information months or even years after a breach. They combine fragments of data from different incidents to build detailed profiles of victims. For that reason, users must develop ongoing security habits that reduce exposure and strengthen digital defenses over time. The following additional protection tips will help you stay safer well beyond the initial fallout of this incident.
1. Use a Password Manager
One of the most effective ways to protect yourself is to stop reusing passwords. A password manager generates and stores complex, unique passwords for every account.
- Eliminates password reuse, which is one of the biggest risks after partial data leaks.
- Automatically fills in strong passwords so you do not have to remember them.
- Alerts you when an account has appeared in a known breach, giving you time to act quickly.
Popular password managers include Bitwarden, 1Password, and Dashlane. By using one, you can ensure that attackers cannot use your Discord email and username to break into accounts on other platforms.
2. Enable Two-Factor Authentication Everywhere
Two-factor authentication (2FA) makes it much harder for attackers to hijack your accounts even if they know your login details. After the Discord data breach, enabling 2FA across all your accounts is critical.
- Use authenticator apps like Google Authenticator, Microsoft Authenticator, or Authy instead of SMS codes.
- Consider hardware keys such as YubiKey for maximum protection.
- Enable 2FA on your email, banking, cloud storage, and gaming accounts.
3. Check if Your Data Appears in Other Breaches
Your information from the Discord data breach may be combined with older leaks to build a complete identity profile. Checking whether your email or username has been exposed before gives you a chance to lock down other accounts before attackers do.
- Use services like Have I Been Pwned to see if your email has appeared in other breaches.
- If your data is listed, update passwords and enable 2FA on those accounts immediately.
- Consider subscribing to a breach monitoring service for ongoing alerts.
4. Review Discord Privacy Settings
Adjusting your privacy and safety settings on Discord helps reduce exposure to future threats. While these settings do not undo the breach, they can minimize risk moving forward.
- Restrict who can send you friend requests. Avoid the “Everyone” option.
- Turn off direct messages from non-friends in servers.
- Revoke permissions from apps or bots you no longer trust.
- Review what personal data Discord uses for analytics and disable it if unnecessary.
5. Stay Alert for Follow-Up Scams
Data breaches often trigger waves of phishing attacks targeting victims directly. With names, emails, and partial payment data exposed, expect scammers to impersonate Discord or your bank.
- Be skeptical of any unexpected emails referencing Nitro subscriptions or support tickets.
- Do not click links in suspicious emails. Instead, type official URLs directly into your browser.
- Never share 2FA codes, passwords, or financial details over email or direct messages.
6. Consider Identity Theft Protection
If your financial data or personal identifiers were involved in the Discord data breach, identity theft protection services can provide added security.
- These services monitor your credit reports and alert you to suspicious activity.
- They may include dark web scanning to see if your data is being sold.
- Some offer insurance and recovery support if your identity is stolen.
7. Run Regular Malware Scans
Attackers may use phishing campaigns tied to the breach to distribute malware. Regular scans help ensure your system is clean and protected.
- Install a reputable anti-malware tool like Malwarebytes.
- Schedule weekly scans to catch new threats early.
- Keep the software updated so it recognizes the latest attacks.
8. Strengthen Overall Digital Hygiene
The Discord data breach should serve as a reminder that cybersecurity is an ongoing process. Strong digital hygiene lowers your risk across all platforms.
- Keep your operating system and software updated.
- Back up important data regularly.
- Use different emails for different types of accounts, such as banking, social, and gaming.
- Limit how much personal information you share publicly online.
Why Long-Term Protection Is Important
The consequences of the Discord data breach may not appear immediately. Cybercriminals often wait to use stolen data or resell it in underground markets months later. Building stronger habits now ensures that even if your information is circulating, attackers will have a harder time turning it into real damage. By combining password managers, 2FA, breach monitoring, and careful privacy practices, you can dramatically reduce the risks created by this and future incidents.
The Bigger Picture: Third-Party Risks
One of the most important lessons from the Discord data breach is that the company itself was not directly hacked. Instead, attackers targeted a third-party customer support provider that had access to sensitive Discord support tickets and user data. This type of supply chain vulnerability is becoming increasingly common in cybersecurity. While outsourcing may help platforms reduce costs or improve efficiency, it also creates more entry points for attackers. Every vendor a company works with becomes part of its security chain, and the chain is only as strong as its weakest link.
Why Third-Party Breaches Are Dangerous
Third-party breaches are particularly damaging for several reasons:
- Hidden exposure: Users did not consent to share their data with an outside vendor. They trusted Discord to keep it secure, not realizing that a contractor had access to their personal details.
- Lack of oversight: Companies often have limited visibility into a vendor’s security controls. If those controls are weak, breaches may go undetected for longer periods.
- Wider attack surface: Each additional vendor relationship increases the number of possible attack points for criminals.
- Regulatory complexity: Different vendors operate under different privacy laws. This makes accountability difficult when something goes wrong.
Examples of Other Third-Party Breaches
The Discord data breach is not unique. Several major incidents in recent years followed the same pattern:
- Okta contractor breach: Attackers compromised a support contractor, exposing sensitive customer information.
- Ticketmaster breach: A cloud provider storing payment data was hacked, leaking millions of customer records.
- Target breach: Attackers used access from a third-party HVAC vendor to steal tens of millions of credit card numbers.
These cases highlight the reality that even large companies with strong internal defenses remain vulnerable if their vendors are insecure. Discord’s reliance on an external support provider fits this troubling pattern.
The Supply Chain Security Problem
From a cybersecurity perspective, supply chain risk is one of the hardest challenges to solve. Modern platforms depend on countless third-party services for support, payment processing, cloud hosting, and analytics. Each of these providers has access to some portion of sensitive data. Users rarely know which companies are handling their information, making it impossible for them to assess the risks directly. In the Discord data breach, users contacting support likely assumed their conversations stayed within Discord. Few expected that a separate vendor was processing their tickets and attachments.
Why Discord’s Vendor Choice Raises Questions
Discord has not revealed which vendor was compromised, but its decision to outsource sensitive support functions raises several critical questions:
- Did Discord conduct a full security audit of the vendor before granting access?
- Were regular audits and monitoring in place to ensure ongoing compliance?
- What contractual obligations did the vendor have regarding breach detection and reporting?
- Why were sensitive attachments, partial payment data, and ticket transcripts stored outside Discord’s own systems?
These unanswered questions make it clear that Discord’s vendor management practices deserve closer scrutiny.
Industry-Wide Implications
The Discord data breach also highlights a larger industry problem. As companies outsource more services, users are increasingly vulnerable to breaches caused by vendors they have never heard of. This creates a gap between user expectations and corporate practices. Regulators are paying attention. Under GDPR in Europe and CCPA in California, companies are responsible for protecting user data even when it is handled by third-party providers. Discord could face investigations or penalties if regulators determine that vendor oversight was inadequate.
What Users Can Do
Unfortunately, individual users cannot control which vendors Discord or other platforms choose to work with. However, you can take steps to limit your exposure:
- Avoid sharing unnecessary personal information in support tickets or attachments.
- Use disposable or secondary emails when contacting customer support for minor issues.
- Stay informed by following ongoing data breach updates, since companies may not disclose vendor-related incidents immediately.
Final Thoughts on Third-Party Risks
The Discord data breach is not just about one company’s failure. It is part of a growing trend where attackers exploit weaknesses in the supply chain rather than attacking the main platform directly. Until companies take vendor oversight as seriously as their own internal defenses, users will remain at risk. For now, the best defense for individuals is to limit the information shared with support teams, use strong security practices across all accounts, and demand greater transparency from the platforms they rely on.
Key Takeaways from the Discord Data Breach
The Discord data breach is a serious incident that exposed sensitive personal information from users who contacted Discord’s Customer Support or Trust and Safety teams. Even though passwords and full credit card numbers were not included, the combination of names, emails, usernames, IP addresses, partial payment details, and private support ticket content is enough to create major risks. Cybercriminals can use this data for phishing, harassment, fraud, identity theft, and targeted scams.
Main Points Users Need to Remember
- What was exposed: Names, Discord usernames, email addresses, IP addresses, limited payment data (last four digits of cards, payment type, purchase history), and content of support tickets including messages and attachments.
- What was not exposed: Account passwords, authentication data, full credit card numbers, CVV codes, physical addresses, and regular Discord chat or server activity.
- Why it matters: Even partial information can be weaponized. Criminals often combine fragments from multiple breaches to create complete profiles and launch convincing social engineering attacks.
- Discord’s response: Notifications were delayed and inconsistent. Some users received emails two weeks after the incident, while others never received one at all. The vague language in the notification left users uncertain about what was actually taken.
- Third-party risks: This breach did not come from Discord’s core systems but from a third-party vendor. It highlights the growing dangers of supply chain security failures.
Immediate Steps for Users
- Change your Discord password and ensure it is unique.
- Enable two-factor authentication (2FA) on Discord and email accounts.
- Review bank and card statements closely for unusual activity.
- Refresh your IP address and consider using a VPN.
- Run a malware scan with Malwarebytes to protect against phishing payloads.
- Be cautious of phishing emails or messages that reference Discord support tickets or Nitro purchases.
The Bigger Lesson
This Discord data breach proves that even if a company’s main systems are secure, your personal information can still be exposed through its vendors. It is a reminder that users must take their own precautions: use unique passwords, enable 2FA, limit the information you share in support tickets, and monitor accounts for unusual activity. At the same time, companies like Discord need to be held accountable for transparency, faster breach notifications, and stronger vendor management practices.
Trust is the foundation of any communication platform. Once that trust is broken, it is difficult to rebuild. By understanding what happened in this breach and taking the steps outlined above, users can protect themselves today and demand stronger protections from the platforms they rely on tomorrow.




