The International Police Association (I.P.A.) Virus
Recent ransomware titled The International Police Association malware has been infecting computers in computers in Austria, Belgium, Switzerland, Germany, Spain, France, Greece, Italy, Finland, Nederland, Poland, Portugal and Sweden. If the infection happened in Spain, this IPA virus will load a Spanish alert message and download Spain’s flag from a remote server (as well for any other country). The IPA virus has recently made it’s appearance in North American countries Canada and the United States, among others, which is when we were alerted of it.
What is The International Police Association Virus?
Alike most other ransomware the IPA virus locks computers or “holds them hostage” by pretending to be the International Police Association and claims the computer user has been associating in cybercrime, child pornography, or zoofilia. To unlock and use the infected computer again the IPA virus demands a fine usually around $50 or $100 to be paid by online credit such as a UKash voucher in European countries. Keep in mind UKash is a legitimate institution and is in no way connected with this malware similar and that other credit systems may be in place due to geographic location of the infected computer.
- Other aliases/families: Win32/LockScreen.CI.Ransomware, Win32/Trojan, Fake Police Malware
- Similar Ransomware: Citadel Reveton, FBI Moneypak

International Police Association (I.P.A.) Symptoms
■ Once the Trojan is executed, it determines the infected computer’s IP address, changes different system settings on the infected computer, creates a full screen window, loads fake alert messages, and continues to download all the necessary graphics from a remote server which are will be used per geographic location as discussed before.
■ The International Police Association (I.P.A.) prevents victims from accessing their computer Desktop and displays a fake warning claiming that the operating system is locked by I.P.A because the computer user was involved with cybercrime which may include watching and/or distributing illegal content such as child pornography or zoofilia related content.
International Police Association (I.P.A.) virus warnings from different countries:
■ Ihr Computer wurde gesperrt
Ihr Computer wurde durch das System der automatischen Informationskontrolle gesperrt
■ Votre ordinateur est bloqué
Votre ordinateur a été bloqué par le système de contrôle automatique informationnel
■ El ordenador suyo esta bloqueado
El ordenador suyo fue bloqueado por el sistema del control informativo automatizado
■ O υπολογιστής σας έχει μπλοκαριστεί
■ Il suo computer è stato bloccato
il suo computer è stato bloccato da sistema di controllo d’informazione automatico
■ Tietokoneenne lukkiutui
■ Uw computer is geblokkeerd
Uw computer is geblokkeerd door het systeem van een automatische informatiecontrole
■ Ten komputer został zablokowany
Ten komputer został zablokowany przez system automatycznej kontroli informacyjnej
■ O seu computador foi bloqueado
O seu computador foi bloqueado pelo sistema do controlo automatico de informação
■ Datorn har blockerats
Datorn har blockerats av ett system för avtomatisk information kontroll
How to remove the International Police Association Virus
The International Police Association (I.P.A.) virus has not been reported to be aggressive but may progress or become bundled with other malware, as well as the possibility of redistribution.
Some users are still able to access the internet correctly, if this is the case please download the free version of Malwarebytes and proceed to scan and remove the IPA infection. But most of the time, unlike other ransomware the IPA virus allows infected computers to reboot in Safe Mode with Networking to download anti-malware software which his then used to scan and remove IPA malware. Another simple solution is to restore your computer to a date and time before your computer became infected with the International Police Virus.
IPA ransomware removal options:
Different victims, depending on location and progression of the infection will require different removal options. Anti-Malware software and restore are the outlined solutions but may require different steps to achieve the initial process.
- Anti-Malware Software – Scan and remove malware
- Regular Installation
- Install using Command Prompt with Networking
- System restore
- Start Menu Restore
- Safe Mode with Command Prompt
- Manual Removal
1. Anti-Malware
[Small_Button class=”lightblue”] Remove Malware [/Small_Button]
Safe Mode With Networking
For users needing access to the Internet or the network they’re connected to. This mode is helpful for when you need to be in Safe Mode to troubleshoot but also need access to the Internet for updates, drivers, removal software, or other files to help troubleshoot your issue.
- This mode will also bypass any issues where Antivirus or Anti Malare applications have been affected/malfunctioning because of the FBI Moneypak infection’s progression.
The plan with this option is to enter your computer in “safe mode with network” and install anti-malware software. Proceed to scan, and remove malicious files.
1. Reboot your computer in “Safe Mode with Networking”. As the computer is booting tap the “F8 key” continuously to reach the correct menu.Use your keyboard to navigate to “Safe Mode with Networking” and press Enter. Shown below.

2. If you can easily access the internet to install removal software do so, otherwise launch Internet Explorer. In Internet Explorer go to: Tools->Internet Options->Connections tab.
Click Lan Settings button and uncheck the checkbox labeled Use a proxy server for your LAN. Click OK.
3. It is now recommended to download Malwarebytes and run a full system scan to remove Antivirus Live malware from your computer if you do not have this application on your system.
2.System Restore
Depending on the progression of the International Police Association ransomware virus, different steps may be needed to simply restore your computer depending on restrictions implied by the IPA infection. Outlined bellow are two different solutions. If you can not perform a start menu restore, proceed to the Safe Mode with Command Prompt restore instructions.
Start Menu Restore
 Standard directions to quickly access Window’s System Restore Wizard.
Standard directions to quickly access Window’s System Restore Wizard.
1. Access windows Start menu and click All Programs.
2. Click and open Accessories, click System Tools, and then click System Restore.
If you are prompted for an administrator password or confirmation, type the password or provide confirmation.
3. Restore your computer to a date and time before infection.
Safe Mode With Command Prompt Restore
If you can not access your operating system, this is the suggested step.
1. Restart/reboot your computer system. Unplug if necessary.
2. Enter your computer in “safe mode with command prompt”. To properly enter safe mode,repeatedly press F8 upon the opening of the boot menu.
3. Once the Command Prompt appears you only have few seconds to type “explorer” and hit Enter. If you fail to do so within 2-3 seconds, the FBI MoneyPak ransomware virus will not allow you to type anymore.
4. Once Windows Explorer shows up browse to:
- Win XP: C:\windows\system32\restore\rstrui.exe and press Enter
- Win Vista/Seven: C:\windows\system32\rstrui.exe and press Enter
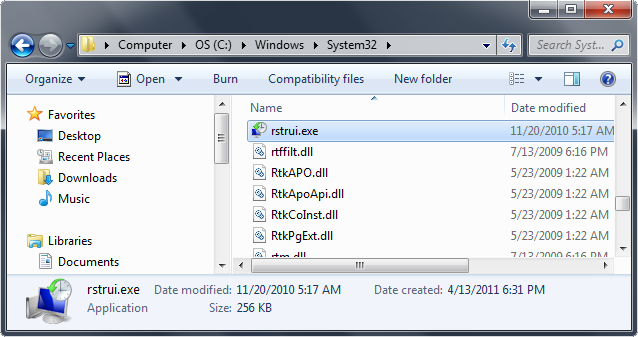
5. Follow all steps to restore or recover your computer system to an earlier time and date, before infection to complete.
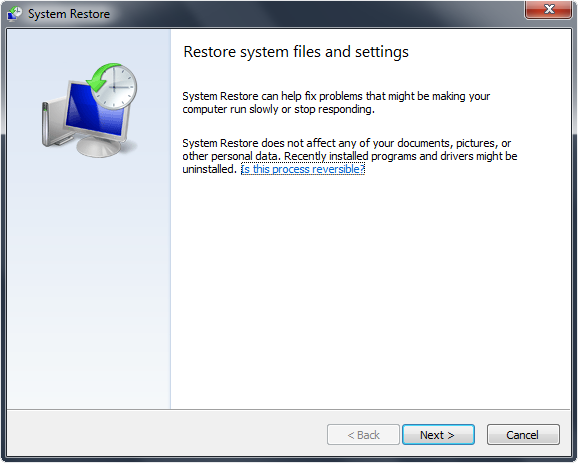
More information on Window’s system restore: http://windows.microsoft.com/en-US/windows-vista/System-Restore-frequently-asked-questions
Safe Mode With Networking
For users needing access to the Internet or the network they’re connected to. This mode is helpful for when you need to be in Safe Mode to troubleshoot but also need access to the Internet for updates, drivers, removal software, or other files to help troubleshoot your issue.
- This mode will also bypass any issues where Antivirus or Anti Malare applications have been affected/malfunctioning because of the International Police Association infection’s progression.
The plan with this option is to enter your computer in “safe mode with network” and install anti-malware software. Proceed to scan, and remove malicious files.
1. Reboot your computer in “Safe Mode with Networking”. As the computer is booting tap the “F8 key” continuously to reach the correct menu.Use your keyboard to navigate to “Safe Mode with Networking” and press Enter. Shown below.

2. If you can easily access the internet to install removal software do so, otherwise launch Internet Explorer. In Internet Explorer go to: Tools->Internet Options->Connections tab.
Click Lan Settings button and uncheck the checkbox labeled Use a proxy server for your LAN. Click OK.
3. It is now recommended to download Malwarebytes and run a full system scan to remove the IPA malware from your computer if you do not have this application on your system.
3. Manual Removal
Outlined below are instructions to kill the fake IPA malware process, remove associated files, and delete registry values associated with the ransomware.
1.Restart your computer. As your computer reboots but before the desktop launches, press “F8″ key constantly. Use the arrow keys to highlight the “Safe Mode with Networking” option, and then press ENTER.
2. Stop the possess of International Police Association. Go to Window’s Task Manager (Alt+Ctrl+Delete) and stop the IPA ransomware process detailed below.
Process name: Protector-[rnd].exe
3. Search for and delete related files from your infected computer.
File to search for and remove: %AppData%\Protector-[rnd].exe
4. Remove the registry entries associated as below in Registry Editor. Type Regedit in the Window’s Start menu and press Enter to bring up the registry editor.
Delete IPA malware registry entries:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_ERROR_PAGE_BYPASS_ZONE_CHECK_FOR_HTTPS_KB954312
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “WarnOnHTTPSToHTTPRedirect” = 0
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableRegedit” = 0
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableRegistryTools” = 0
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableTaskMgr” = 0
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “Inspector”
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings “ID” = 0
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings “net” = “2012-2-17_2”
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings “UID” = “rudbxijemb”
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\_avp32.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\_avpcc.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ashDisp.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\divx.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mostat.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\platin.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tapinstall.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File












oh thank you so much it is really helpful. it did work for me. the stupidest thing when i call for 1888…nuber they asked me $146 to remove it.
the explorere system work good thanks hoooo