An alleged iOS 26 Zero Day exploit has appeared for sale on a dark web marketplace, with a threat actor claiming to possess a full chain attack capable of remotely compromising modern iPhones and iPads. The listing, published by a seller using the alias ResearcherX, describes a memory corruption flaw inside the iOS Message Parser that can be triggered through a malicious message payload without any user interaction. If accurate, this alleged iOS 26 Zero Day represents one of the most serious mobile security threats to emerge since the release of iOS 26.
The seller states that the exploit delivers complete remote code execution, a sandbox escape, and a kernel level privilege escalation, ultimately providing root access to the device. This type of vulnerability chain is extremely rare and is often associated with high level espionage operations, commercial spyware developers, and state aligned threat groups. The appearance of a claimed iOS 26 Zero Day so soon after the OS release has attracted the attention of researchers monitoring dark web exploit markets.
Details of the Alleged iOS 26 Zero Day Listing
The listing asserts that the exploit targets the iOS 26 Message Parser, an attack surface that processes untrusted message data automatically. Historically, this subsystem has been linked to several high profile espionage campaigns due to its automatic handling of complex content. The claimed iOS 26 Zero Day relies on a memory corruption bug within this parser to achieve the initial foothold.
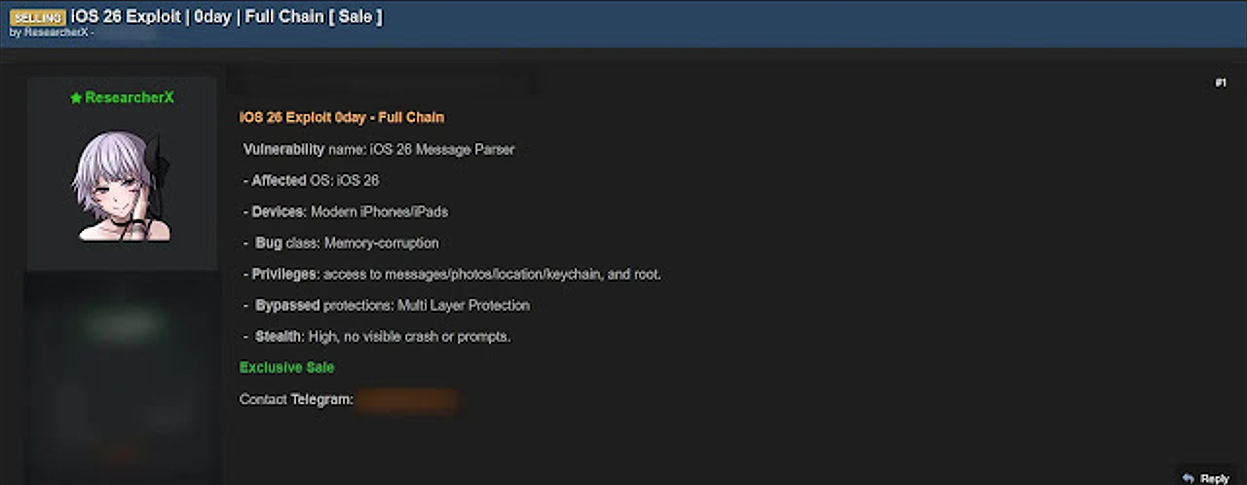
The dark web advertisement includes the following technical claims:
- Attack vector: Malformed message payload processed automatically by iOS 26.
- Bug class: Memory corruption affecting the message parsing engine.
- Impact: Full remote code execution on targeted devices.
- Bypasses: Multi Layer Protection introduced in iOS 26.
- Privileges: Access to messages, photos, location, Keychain, and full root.
- Stealth level: No visible crash logs, prompts, or device alerts.
- Compatibility: Modern iPhones and iPads running iOS 26.
The actor has marked the listing as an exclusive sale, meaning the exploit will allegedly be sold to a single buyer. Exclusive full chain iOS vulnerabilities commonly command prices between two and five million dollars depending on reliability, stealth, and device coverage. If the claimed iOS 26 Zero Day is functional, it would fall within this tier of high value offensive capabilities.
Why a Full Chain iOS 26 Zero Day Matters
Apple’s mobile security ecosystem is built around multiple layers of isolation, memory protection, and hardware enforced integrity checks. A full chain exploit that breaks through each layer represents one of the most advanced forms of mobile compromise. The alleged iOS 26 Zero Day claims to combine three major components:
- An initial memory corruption flaw triggered automatically by message parsing.
- A sandbox escape that moves execution outside the restricted processing environment.
- A kernel level escalation that grants full system control with persistent root privileges.
Chains of this nature are exceptionally difficult to develop. They typically require deep internal knowledge of iOS internals and access to advanced debugging environments. Only a small number of research labs and threat actors possess the capability to create a full chain of this complexity. This is why the alleged iOS 26 Zero Day immediately drew attention from security researchers and threat intelligence analysts.
Potential Impact if the Exploit Is Genuine
If the iOS 26 Zero Day is authentic, the level of access it provides could expose large volumes of sensitive data from targeted devices. Memory corruption attacks that bypass multiple protection layers often allow access to:
- Encrypted messages and attachments stored locally on the device.
- Full photo and video libraries.
- Real time GPS location and historical movement data.
- Keychain passwords, authentication tokens, and encryption keys.
- Cloud service credentials that permit remote account access.
The seller claims the exploit produces no visible alerts or crashes, which would allow for silent persistence on compromised devices. In past operations, similar vulnerabilities have been used to install highly advanced spyware capable of real time monitoring, microphone activation, camera access, and stealthy data exfiltration.
Security Context Surrounding iOS 26
The iOS 26 release in September 2025 introduced new defensive measures intended to reduce exploit viability. These included expanded parser isolation, hardened kernel boundaries, and additional memory safety checks. If the iOS 26 Message Parser contains a new memory corruption flaw that bypasses these protections, it would indicate a significant architectural oversight within the recent redesign.
Zero day discovery activity typically spikes after major operating system updates. Attackers frequently review new code to identify flaws introduced during software refactoring. It is common for high value vulnerabilities to be discovered shortly after major platform changes, and the alleged iOS 26 Zero Day could be a product of this window of opportunity.
Legitimacy and Verification Challenges
As with all dark web exploit listings, independent verification remains difficult. Threat actors often exaggerate or fabricate capabilities to attract buyers. Screenshots from the listing show a typical structured sale format, but no technical proof of execution has been released. This means the claim cannot currently be validated.
Despite the uncertainty, the technical details align with realistic mobile exploit methodologies. Past zero click vulnerabilities have frequently targeted message parsing engines because they process attacker controlled data automatically and provide broad attack surface coverage across the entire device ecosystem. This increases the plausibility of an iOS 26 Message Parser flaw, although confirmation has not yet been obtained.
Monitoring and Expected Industry Response
Security researchers are expected to increase surveillance of dark web markets to track potential updates, proof of concept materials, or confirmed buyers. If the iOS 26 Zero Day is valid, private notifications may already be underway through coordinated disclosure channels.
Apple often issues rapid out of band patches for critical memory corruption vulnerabilities. A fix may appear in upcoming versions such as iOS 26.0.2 or iOS 26.1 if internal validation confirms an exploitable parsing flaw. Organizations that rely on mobile security for sensitive communications may also issue internal alerts instructing high risk staff to watch for future emergency updates.
The appearance of an alleged iOS 26 Zero Day highlights the importance of rapid patching, secure device hygiene, and continuous monitoring of high value mobile platforms. We will continue tracking developments related to the listing and will update readers as new information becomes available.



