In 2012 we discovered ransomware that was imitating the FBI in hopes to extort currency from unsuspecting victims. We coined the term FBI due to our findings and were the first and only website to publish information about this computer virus. Now a days, a lot has evolved with ransomware in the United States. Some ransomware will still pretend to be the FBI but the that threat of the FBI is becoming more obsolete as people are no longer tricked into believing it.

The FBI virus is still around but a lot has changed. Ransomware has moved away from only restricting access to a victim’s computer to encrypting, deleting, or storing files in a password locked archive. This allows the malware authors to hold files on the computer for ransom instead of the entire machine by promising victims a way to decrypt, decode, or recover encrypted, password-locked, or deleted files.
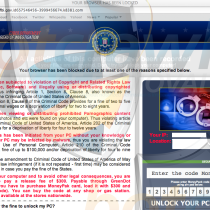
The term FBI virus can be used to describe many variants of ransomware that uses a FBI logo or claims to be the FBI. The FBI virus is essentially a computer virus (ransomware) that locks access to a computer system, displays a message that claims to be from the FBI stating that the computer was involved in prohibited activities, and demands a payment in order to unlock the computer and avoid penalties or jail-time from the FBI. The FBI virus can also refer to ransomware that encrypts files on a computer, changes the filenames, adds a new file extension, and ultimately holds the files ransom for a hefty fee.
If your computer has been locked or encrypted by an a source that claims to be the FBI then you are infected with the FBI virus. However, do not be alarmed because the FBI did not actually lock your computer or corrupt the files on your computer. You are not in trouble with the FBI if this happens to you. This is a computer virus that is in no way, shape, or form associated with the FBI or any legitimate government agency.
If your computer is infected with the FBI virus it may become locked and a full-screen window may appear that claims to contain a message from the FBI. The fake FBI message usually claims that the computer was used illegally and in order to avoid jail-time or other consequences the computer owner must pay a fine via Greendot MoneyPak cards, UKash Vouchers, REloadit, Ultimate Gaming Cards, Bitcoins, PayPal, or other online payment or credit sources.
It is not recommended to pay ransomware authors to decrypt your files. This will only support their activities. Instead you can use programs like Shadow Explorer or Recuva to try and restore corrupted files if you were not able to decrypt your files for free.
Aliases: FBI virus, FBI ransomware, FBI MoneyPak virus
 FBI Virus Removal Guide
FBI Virus Removal Guide
1. Download and Install Malwarebytes Anti-Malware software to detect and remove malicious files from your computer.
2. Open Malwarebytes and click the Scan Now button – or go to the Scan tab and click the Start Scan button.
3. Once the Malwarebytes scan is complete click the Remove Selected button.
4. To finish the Malwarebytes scan and remove detected threats click the Finish button and restart your computer if promoted to do so.
5. Download and Install HitmanPro by Surfright to perform a second-opinion scan.
6. Open HitmanPro and click Next to start scanning your computer. *If you are using the free version you may chose to create a copy or perform a one-time scan.
7. Once the HitmanPro scan is complete click the Next button.
8. To activate the free version of HitmanPro: enter your email address twice and click the Activate button.
9. Click the Reboot button.
10. Download and Install CCleaner by Piriform to cleanup junk files, repair your registry, and manage settings that may have been changed.
11. Open CCleaner and go to the main Cleaner screen. Click the Analyze button. When the process is complete, click the Run Cleaner button on the bottom right of the program interface.
12. Go to Tools > Startup and search for suspicious entries in each tab starting from Windows all the way to Content Menu. If you find anything suspicious click it and click the Delete button to remove it.
13. Go to the Registry window and click the Scan for Issues button. When the scan is complete click the Fix selected issues… button and click Fix All Selected Issues.
This troubleshooting guide to remove FBI ransomware contains different options to remove this infection.
- Manual FBI virus removal instructions
- System Restore/Recovery or Reset
- Safe Mode with Networking
- Flash Drive
- Optical CD-R
- Slave Hard Disk Drive
Manual FBI virus removal
1. Open Windows Start Menu, type %appdata% into the search field, and press Enter.
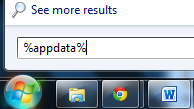
2. Go to: Microsoft\Windows\Start Menu\Programs\Startup
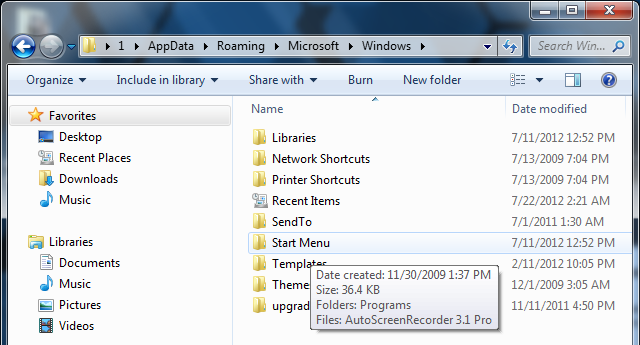
3. Remove ctfmon (ctfmon.lnk if in dos). This is what’s calling the virus on start up. This is not ctfmon.exe.
4. Open Windows Start Menu, type %userprofile% into the search field, and press enter.

5. Go to: Appdata\Local\Temp
6. Remove rool0_pk.exe,[random].mof , and V.class
The virus files may have names other than “rool0_pk.exe” but file names should appear similar with the same style of markup. There may also be 2 files, 1 being a .mof file. Removing the .exe file will fix FBI Moneypak. The class file uses a java vulnerability to install the virus and removal of V.class is done for safe measure.
FBI Moneypak Files:
The files listed below are a collection of what causes FBI Moneypak to function. To ensure FBI Moneypak is completely removed via manually, delete all given files if located. Keep in mind, [random] can be any sequence of numbers or letters and some files may not be found in your infection.
%Program Files%\FBI Moneypak Virus %Appdata%\skype.dat %Appdata%\skype.ini %AppData%\Protector-[rnd].exe %AppData%\Inspector-[rnd].exe %AppData%\vsdsrv32.exe %AppData%\result.db %AppData%\jork_0_typ_col.exe %appdata%\[random].exe %Windows%\system32\[random].exe %Documents and Settings%\[UserName]\Application Data\[random].exe %Documents and Settings%\[UserName]\Desktop\[random].lnk %Documents and Settings%\All Users\Application Data\FBI Moneypak Virus %CommonStartMenu%\Programs\FBI Moneypak Virus.lnk %Temp%\0_0u_l.exe %Temp%\[RANDOM].exe %StartupFolder%\wpbt0.dll %StartupFolder%\ctfmon.lnk %StartupFolder%\ch810.exe %UserProfile%\Desktop\FBI Moneypak Virus.lnk WARNING.txt V.class cconf.txt.enc tpl_0_c.exe irb700.exe dtresfflsceez.exe tpl_0_c.exe ch810.exe 0_0u_l.exe [random].exe
End ROGUE_NAME Processes:
Access Windows Task Manager (Ctrl+Alt+Delete) and kill the rogue FBI Moneypak process. Please note the infection will have a random name for the process [random] which may contain a sequence of numbers and letters (ie: USYHEY347H372.exe).
[random].exe
Remove Registry Values:
To access Window’s Registry Editor type regedit into the Windows Start Menu text field and press Enter.

HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\[random].exe HKEY_LOCAL_MACHINE\SOFTWARE\FBI Moneypak Virus HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Policies\System ‘DisableRegistryTools’ = 0 HKEY_LOCAL_MACHINE \SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system ‘EnableLUA’ = 0 HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Internet Settings ‘WarnOnHTTPSToHTTPRedirect’ = 0 HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Policies\System ‘DisableRegedit’= 0 HKEY_CURRENT_USER\Software\FBI Moneypak Virus HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run ‘Inspector’ HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\FBI Moneypak Virus HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Policies\System ‘DisableTaskMgr’ = 0 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Inspector %AppData%\Protector-[rnd].exe HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\WarnOnHTTPSToHTTPRedirect 0 HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\ID 4 HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\UID [rnd] HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\net [date of installation] HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorAdmin 0 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorUser 0 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA 0 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\Debugger svchost.exe HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\Debugger svchost.exe HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE\Debugger svchost.exe HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableRegistryTools” = 0 HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableTaskMgr” = 0 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “ConsentPromptBehaviorAdmin” = 0 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “ConsentPromptBehaviorUser” = 0 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “EnableLUA” = 0
System Restore – Recovery
Below we detail 3 different instructions to restore or recover a common Window’s computer.
Windows Start Menu Rstrui.exe Restore
- Access Windows Start menu
- Type rstrui.exe into the search field and press Enter
- Follow instructions in Window’s Restore Wizard
Start Menu Restore
- Access Windows Start menu and click All Programs.
- Click and open Accessories, click System Tools, and then click System Restore. If you are prompted for an administrator password or confirmation, type the password or provide confirmation.
- Follow the simple instructions to Restore your computer to a date and time before infection.
Safe Mode With Command Prompt Restore
If you can not access Window’s desktop, this is the suggested step. If it is difficult to start windows in safe mode; if Windows’s brings up a black screen, with “safe mode” in the four corners – Move your cursor to the lower left corner, where the Search box is usually visible in Windows Start Menu and it will come up, including the “Run” box.
1. Restart/reboot your computer system. Unplug if necessary.
2. Enter your computer in “safe mode with command prompt”. To properly enter safe mode, repeatedly press F8 upon the opening of the boot menu.
3. Once the Command Prompt appears you only have few seconds to type “explorer” and hit Enter. If you fail to do so within 2-3 seconds, the FBI MoneyPak ransomware virus will not allow you to type anymore.
4. Once Windows Explorer shows up browse to:
- Win XP: C:\windows\system32\restore\rstrui.exe and press Enter
- Win Vista/Seven: C:\windows\system32\rstrui.exe and press Enter
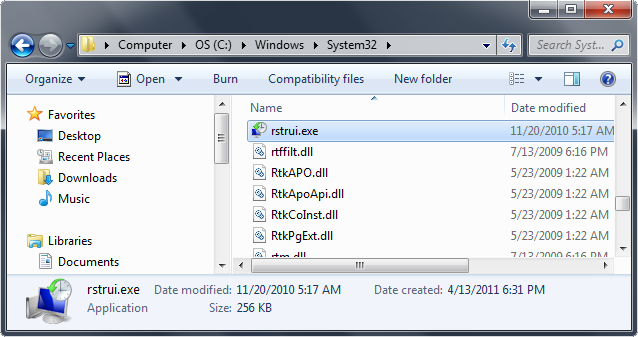
5. Follow all steps to restore or recover your computer system to an earlier time and date (restore point), before infection.
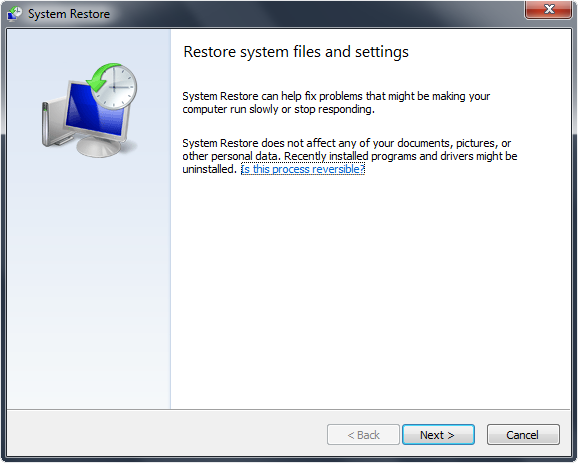
Safe Mode with Networking
For users needing access to the Internet or the network they’re connected to. This mode is helpful for when you need to be in Safe Mode to troubleshoot but also need access to the Internet for updates, drivers, removal software, or other files to help troubleshoot your issue.
- This mode will also bypass any issues where Antivirus or Anti Malare applications have been affected/malfunctioning because of the FBI Moneypak infection’s progression.
The plan with this option is to enter your computer in “safe mode with network” and install anti-malware software. Proceed to scan, and remove malicious files.
1. Reboot your computer in “Safe Mode with Networking”. As the computer is booting (when it reaches the manufacture’s logo) tap and hold the “F8 key” continuously to reach the correct menu. On the Advanced Boot Options screen, use your keyboard to navigate to “Safe Mode with Networking” and press Enter. Shown below.
- Make sure to log into an account with administrator rights.
The screen may appear black with the words “safe mode” in all four corners. Click your mouse where windows start menu is to bring up necessary browsing.

2. There are a few different things you can do…
- Pull-up the Start menu, enter All Programs and access the StartUp folder.
- Remove “ctfmon” link (or similar).
This seems to be an easy step in removing the FBI virus for many users. If you are interested in learning about ctfmon.exe please click here.
Now, move on to the next steps (which is not a necessity if you removed the file above but provides separate options for troubleshooting).
3. If you still can’t access the Internet after restarting in safe mode, try resetting your Internet Explorer proxy settings. These 2 separate options and following steps will reset the proxy settings in the Windows registry so that you can access the Internet again.
How To Reset Internet Explorer Proxy Settings
- Option 1
In Windows 7 click the Start button. In the search box type run and in the list of results click Run.
In Windows Vista click the Start button and then click Run.
In Windows XP click Start and then click Run.
Copy and paste or type the following text in the Open box in the Run dialog box and click OK:
reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings" /v ProxyEnable /t REG_DWORD /d 0 /f
In Windows 7 click the Start button. In the search box type run and in the list of results click Run.
In Windows Vista click the Start button and then click Run.
In Windows XP click Start and then click Run.
Copy and paste or type the following text in the Open box in the Run dialog box and click OK:
reg delete "HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings" /v ProxyServer /f
Restart Internet Explorer and then follow the steps listed previously to run the scanner
- Option 2
Launch Internet Explorer. In Internet Explorer go to: Tools->Internet Options->Connections tab.
Click Lan Settings button and uncheck the checkbox labeled Use a proxy server for your LAN. Click OK.
4. It is now recommended to download Malwarebytes (free or paid version) and run a full system scan to remove FBI Moneypak malware from your computer if you do not have this application on your system.
Flash Drive
- Turn off your computer system and Unplug your internet connection
- Turn the machine back on (In some cases the virus can only open if your machine is plugged into the internet)
- On another (clean) computer, download Malwarebytes or your preferred removal program and load the Mbam-Setup.exe (or similar) file onto the flash drive
- Remove the flash drive from the clean computer and insert it into the affected machine, proceed to install Malwarebytes (etc) using the setup file located on the flash drive.
- Run a full system scan, Malwarebytes will find and eradicate malicious files
- Restart your machine
Optical CD-R
- Place a blank CD-R into your CDROM drive
- Download and place Microsoft Defender or your prefered removal program onto the blank CD-R
- Restart your computer and boot from CD
“You may need an old school keyboard (not the USB, but the PC connector type) since the virus delays the USB startup. The Defender will clean your PC in totality. This virus is somehow complex, but is no match for Windows Defender. After the scan is complete, run again a full scan without a restart.”
Slave Hard Disk Drive
If you are having complications with Anti-Malware software a suggestion would be to slave your HDD, then proceed to scan. You will need a second operating computer and tools to remove your hard drive. *Please note this may be difficult for some users and there are other options to scan your hard drive during complications. This is a common practice for local computer technicians.
- Remove the Hard Disk Drive from your computer.
- On the circuit board side of your HDD set the drive to “slave”.
- Connect the slave drive to an unaffected computer.
- Scan the slave drive, and proceed to remove any malware on the drive. Make sure to scan each user account.
- Reconnect the HDD to your original computer.
The key to staying protected against future infections is to follow common online guidelines and take advantage of reputable Antivirus and Anti-Malware security software with real-time protection.
Real-time security software
Security software like Malwarebytes and Norton Security have real-time features that can block malicious files before they spread across your computer. These programs bundled together can establish a wall between your computer and cyber criminals.
- Backup your computer and personal files to an external drive or online backup service
- Create a restore point on your computer in case you need to restore your computer to a date before infection
- Avoid downloading and installing apps, browser extensions, and programs you are not familiar with
- Avoid downloading and installing apps, browser extensions, and programs from websites you are not familiar with – some websites use their own download manager to bundle additional programs with the initial download
- If you plan to download and install freeware, open source software, or shareware make sure to be alert when you install the object and read all the instructions presented by the download manager
- Avoid torrents and P2P clients
- Do not open email messages from senders you do not know





























Thank you for the instructions! I used the steps in the forum for creating accounts
sean you are really hot <3
Thank you so much!! It worked !
Thank you for the tutorial on how to get rid of the FBI ransom ware. My 17 year old son was trying to download an application on his laptop at what he thought was a Boy Scout affiliated website and got the ransom ware instead. I had heard of it at work but couldn’t remember how to get rid of it. Now I’d just like to figure out who developed it and bring them to justice by which I mean
put a bullet in their worthless head.Thanks again.Thank you for providing this valuable information. Restoring from safe mode helps
I figured out the System Restore in Safe Mode method myself, but it’s good to see a confirmation here that it did remove the threat entirely.
You guys are awesome! Allready had that malware once but this time it was waay harder to get away. Thanks for all those different methods
Good God, you should get an award or something for this free and thorough guide. I thought I had to buy another laptop, you completely saved me. Many thanks!
Thank you soooo much!!!!!
Opening with command promt and typing explorer is what saved me. Holy crap this was a nasty bug. It forced me to shut down in regular safe mode.
I finally managed to enter rstrui.exe at the command prompt and restored system. THANK YOU!!
Tried Malwarebytes free version which worked in about 15 minutes. I’ll gladly pay the $25 scan regularly.
instead of going to safe mode select System Restore. Restore it to a day+ before the problem started to occur. That worked for me.
I bet all you people that did download child porn just about crapped your pants
Finally I am able to fix it …
I was affected couple of days ago and it was so annoying, as I was not able to run any anti-virus, as it shows white screen and nothing can be done.
Luckily I have 2 user accounts (admin and Guest), From guest account I provided access to admin files ..like c:/users/admin_acct/appdata and local , roaming, temp all locations as provided as solution 2 above
Then I ran malwarebytes from guest acc, it deleted all malware in admin accoutn and I am done
It’s no point blaming the FBI for infecting their computer with such ransomware that disguise itself as FBI, whether it is FBI Anti-Piracy Warning or similar. The FBI has been aware for a long time, and yet it is still evolving. It’s one thing to keep the anti-malware and anti-virus solutions updated as well as operating system security updates to prevent infections.
How long should the system restore take after the safe mode command prompt boot up to remove this disgusting virus…
This is the second time we got it but this time it displayed child porn thumbnail pics!!! I was having a seizure trying to get away from it!!! I hope whoever is responsible for this slop finds forgiveness a higher power – they’re not getting it in this life! So sick and tired of this hacking crap – can’t get a real job!
I had this virus on Windows XP and this virus did not funtion unless it was connected to the inernet. I started my AVG anti virus to download updates and then connected to the internet. AVG picked it up right away and I was able to expell it.
Than you. I had hard time with this virus, until I found your post. After I could reach explorer was easy pie.
I’M STILL SOMEWHAT OF A COMPUTER DUMMY
I BOUGHT A NEW COMPUTER PLANNIN TO GIVE OLD ONE TO MY BROTHER
WHEN I GET THIS VIRUS PACK ON HIS COMPUTER
AFTER SCANNIN AND LOOKIN FOR VIRUS REMOVAL
AFTER 2 FAILURES
YOU’RE ADDRESS CAUGHT MY EYE
WAS ABLE TO REACH SYSTEMS RESTORE
COMPUTER SCREEN/TOOLBARS CAME BACK ON
EVERTHING LOOKS GOOD I’M GONNA DOWNLOAD
ANTIVIRUS NOW
THANK YOU VERY MUCH
SINCERLY STEVE
turn off your damn caps lock.
Excellent sugestion. It was very useful. Thanks a lot.
Thank you!! I was freaking out!
“Malware has blocked and quarantined a treat.” Beatiful!
THANK YOU THANK YOU THANK YOU!!! I was able to get in through safe with command and do a system restore. Should I still go back and do a check for manual removal?
Thank you! I just got this FBI virus and you’ve just saved me! THANK YOU SO MUCH
I solved mine in a way I haven’t read about.
In Windows 7 I wasn’t able to get into safe mode (endless boot loop), and was almost completely locked out in regular mode. I had the ransom page displayed in full screen. Ctrl+Alt+Del brought up the normal screen, but task manager would not work.
Out of frustration I started clicking the links on the ransom page just so I could see something different (how much worse could it get?) I believe the key was clicking on the email link at the bottom of the page (you’ll see why later). I hit Ctrl+Alt+Del -> Shut Down to make my next attempt at a new strategy. When I did, the shut down hung up asking if I wanted to force Outlook to close. Apparently hitting the email link had launched Outlook in the background. I IMMEDIATELY hit CANCEL when Windows asked if I would like to force Outlook to close before Windows had a chance to close it and continue the shut down. The shutdown stopped, but the virus processes had already ended in prep for shutdown. I had my computer back, but still had to remove the virus with MalwareBytes.
I hope this can help someone else.
thanks a lot!
YOU PERVERTS!! ALL OF YOU!! and me too….
I don’t know how to thank you. so far it worked with system restore. My malaware for some reason was off. thank you again
The system restore procedure worked. Thank you very much!!
I wonder how many people fell for this, and how much money the person made…
Omg THANK YOU
Did the restore thank you so much it’s great to have people like you for help your a lifesaver it worked great to get rid of it my uncle also thanks you since it was his computer I fixed with ur help
This site was a real lifesaver for us. We were able to remove the virus using the system restore suggestion. Will be getting some anti malware for sure. Thanks again…
excellent explainations…corrected problem. Thank you
I booted up with “enable VGA mode”. The FBI virus initially blocked everything. I left it running without doing anything for about 15 minutes; magically the FBI disappeared and I was able to use system restore. The screen layout was distorted but still workable. Hope this will work for you too.
Thanks for the guide..found this on my dad’s laptop, he really doesn’t know about computers (neither do I) but I’m on the internets a lot more and knew this was probably a virus with a quick fix. He was about to take it to the computer shop tomorrow and gave me $$ for removing it 😀
😀
Thank you so much for the help!!! i was so scared!!
I must have a newer version of the malware as the version i had disabled the ability to restart in safe mode. if you tried, you get the blue screen. So here is what worked for me…
Once i disabled my internet I was able to get on to my pc pretty easily. you have a few options here depending on how you connect. If you have a desk top, just unplug the network cable. Some laptop’s have a switch on the outside that you can just turn the network off, but others you might have to disconnect your router or modem.
now that you no longer have an internet connection, turn on your computer and all should seem normal.it seems to be tricked some way by not having an internet connection( of i should say this was my experience).
i went into control panel and created a new user with admin privileges. i then restarted the computer and logged in on the new account i just created. all seems to be fine. I restored the internet connection and then went to malwarebytes.org and downloaded the free version(when you install uncheck the trial of the pro version). after you install, run the update so you have the latest definition files and run a Full scan on your computer. after the scan is done, let it repair the files it has identified.
i then turned the internet connection off again and restarted the computer. When it came back up, i logged on under the original account and ran Malware bytes that was installed from the other account( it will appear on both). it found a few more trojan’s which I removed after the scan was complete. Your computer will restart after it removes the trojan’s. Everthing seems normal now, so i deleted the second account that was created above.. good luck with this nasty malware..
Tom, great comments, worked perfectly for me. Thank you very much. Best regards.
Seems to have worked so far! Your info was the only thing that has let me do anything so far!
I was able to download Malwarebytes, but now every second a notice pops up that says the program has blocked & quarantined a threat svchost.exe Trojan.Agent – does this ever stop or will the Virus continue to try and attach my computer?
There is a way to stop that, contact Malwarebytes Support for that
Thx for guide I seriously almost cried when this fbi thing popped up
The only way I could get rid of the virus was to start-up in safe mode with command prompt and run malwarebytes from the command line.
I got the virus today (Dec. 27). Perhaps it is a new/nastier version. In safe mode and safe mode w/networking, I get a blank white screen within a few seconds of windows booting up. I already have malwarebytes on my computer and can try to activate it, and believe it starts, but almost immediately the white screen comes up and I can’t do or see anything. Note that it is just a blank white screen, without the FBI scam verbage. When I power down, just before the machine turns off, the white screen disappears, and I can see my desktop.
I can get the task manager option screen with
, but no matter what option I take, it just puts me back to the blank white screen.I tried the system restore option via the command prompt. It did not work as expected, but eventually (somehow) I got the user interface to open and I selected a restore point from a few days ago. After a considerable amount of time running, the system restore failed due to lack of memory space (not sure if that is legit or nonsense from the virus).
Any help is appreciated.
Thank You so much downloaded software already and read about the restore option so i will try it tomorrow.
A new computer virus which claims you have violated copyright laws is making the rounds. This type of virus is known as ransomware because it locks your computer and demands a payment to unlock it. What should you do if you become a victim of this virus? First, don’t pay the “fine.” Second, you can take your computer to a repair service or if you feel more technically incline you can attempt to remove the virus yourself. http://botcrawl.com/how-to-remove-the-fbi-moneypak-ransomware-virus-fake-fbi-malware-removal/
I did a system restore and it worked perfectly! I was in a panic for an hour before I tried this.
if u do pay the £100 what do u do then?
Malware may still be running in the background. You can contact Green Dot (Moneypak), or whomever you used to pay the fine… I have heard some of them have offered refunds (don’t quote me though).
Suggestions:
■ Run a full-system scan with reputable Antivirus (or AM) software.
■ Perform a System Restore to a date and time before infection.
Hope this helps!
I deleted the account that had the virud and ran a scan and the virus didnt show up, am i safe?
the virus only affects one account when i deleted the account i also deleted the files on the acoount
I can’t technically say yes, but you should be fine.
Make sure you run a full-system scan with reputable Antivirus (or AM) software that has experience removing this particular infection.
It took me about 5 minutes to “remove” this, just got it 10 mins ago, system restore to a restore point I had made and bam. Now to see if my Empire total war saves got saved as well…
Thank you very much