In 2012 we discovered ransomware that was imitating the FBI in hopes to extort currency from unsuspecting victims. We coined the term FBI due to our findings and were the first and only website to publish information about this computer virus. Now a days, a lot has evolved with ransomware in the United States. Some ransomware will still pretend to be the FBI but the that threat of the FBI is becoming more obsolete as people are no longer tricked into believing it.

The FBI virus is still around but a lot has changed. Ransomware has moved away from only restricting access to a victim’s computer to encrypting, deleting, or storing files in a password locked archive. This allows the malware authors to hold files on the computer for ransom instead of the entire machine by promising victims a way to decrypt, decode, or recover encrypted, password-locked, or deleted files.
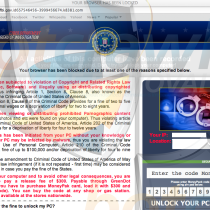
The term FBI virus can be used to describe many variants of ransomware that uses a FBI logo or claims to be the FBI. The FBI virus is essentially a computer virus (ransomware) that locks access to a computer system, displays a message that claims to be from the FBI stating that the computer was involved in prohibited activities, and demands a payment in order to unlock the computer and avoid penalties or jail-time from the FBI. The FBI virus can also refer to ransomware that encrypts files on a computer, changes the filenames, adds a new file extension, and ultimately holds the files ransom for a hefty fee.
If your computer has been locked or encrypted by an a source that claims to be the FBI then you are infected with the FBI virus. However, do not be alarmed because the FBI did not actually lock your computer or corrupt the files on your computer. You are not in trouble with the FBI if this happens to you. This is a computer virus that is in no way, shape, or form associated with the FBI or any legitimate government agency.
If your computer is infected with the FBI virus it may become locked and a full-screen window may appear that claims to contain a message from the FBI. The fake FBI message usually claims that the computer was used illegally and in order to avoid jail-time or other consequences the computer owner must pay a fine via Greendot MoneyPak cards, UKash Vouchers, REloadit, Ultimate Gaming Cards, Bitcoins, PayPal, or other online payment or credit sources.
It is not recommended to pay ransomware authors to decrypt your files. This will only support their activities. Instead you can use programs like Shadow Explorer or Recuva to try and restore corrupted files if you were not able to decrypt your files for free.
Aliases: FBI virus, FBI ransomware, FBI MoneyPak virus
 FBI Virus Removal Guide
FBI Virus Removal Guide
1. Download and Install Malwarebytes Anti-Malware software to detect and remove malicious files from your computer.
2. Open Malwarebytes and click the Scan Now button – or go to the Scan tab and click the Start Scan button.
3. Once the Malwarebytes scan is complete click the Remove Selected button.
4. To finish the Malwarebytes scan and remove detected threats click the Finish button and restart your computer if promoted to do so.
5. Download and Install HitmanPro by Surfright to perform a second-opinion scan.
6. Open HitmanPro and click Next to start scanning your computer. *If you are using the free version you may chose to create a copy or perform a one-time scan.
7. Once the HitmanPro scan is complete click the Next button.
8. To activate the free version of HitmanPro: enter your email address twice and click the Activate button.
9. Click the Reboot button.
10. Download and Install CCleaner by Piriform to cleanup junk files, repair your registry, and manage settings that may have been changed.
11. Open CCleaner and go to the main Cleaner screen. Click the Analyze button. When the process is complete, click the Run Cleaner button on the bottom right of the program interface.
12. Go to Tools > Startup and search for suspicious entries in each tab starting from Windows all the way to Content Menu. If you find anything suspicious click it and click the Delete button to remove it.
13. Go to the Registry window and click the Scan for Issues button. When the scan is complete click the Fix selected issues… button and click Fix All Selected Issues.
This troubleshooting guide to remove FBI ransomware contains different options to remove this infection.
- Manual FBI virus removal instructions
- System Restore/Recovery or Reset
- Safe Mode with Networking
- Flash Drive
- Optical CD-R
- Slave Hard Disk Drive
Manual FBI virus removal
1. Open Windows Start Menu, type %appdata% into the search field, and press Enter.
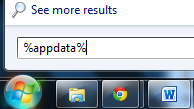
2. Go to: Microsoft\Windows\Start Menu\Programs\Startup
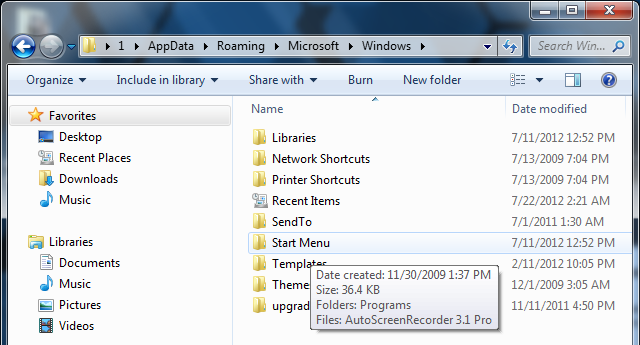
3. Remove ctfmon (ctfmon.lnk if in dos). This is what’s calling the virus on start up. This is not ctfmon.exe.
4. Open Windows Start Menu, type %userprofile% into the search field, and press enter.

5. Go to: Appdata\Local\Temp
6. Remove rool0_pk.exe,[random].mof , and V.class
The virus files may have names other than “rool0_pk.exe” but file names should appear similar with the same style of markup. There may also be 2 files, 1 being a .mof file. Removing the .exe file will fix FBI Moneypak. The class file uses a java vulnerability to install the virus and removal of V.class is done for safe measure.
FBI Moneypak Files:
The files listed below are a collection of what causes FBI Moneypak to function. To ensure FBI Moneypak is completely removed via manually, delete all given files if located. Keep in mind, [random] can be any sequence of numbers or letters and some files may not be found in your infection.
%Program Files%\FBI Moneypak Virus %Appdata%\skype.dat %Appdata%\skype.ini %AppData%\Protector-[rnd].exe %AppData%\Inspector-[rnd].exe %AppData%\vsdsrv32.exe %AppData%\result.db %AppData%\jork_0_typ_col.exe %appdata%\[random].exe %Windows%\system32\[random].exe %Documents and Settings%\[UserName]\Application Data\[random].exe %Documents and Settings%\[UserName]\Desktop\[random].lnk %Documents and Settings%\All Users\Application Data\FBI Moneypak Virus %CommonStartMenu%\Programs\FBI Moneypak Virus.lnk %Temp%\0_0u_l.exe %Temp%\[RANDOM].exe %StartupFolder%\wpbt0.dll %StartupFolder%\ctfmon.lnk %StartupFolder%\ch810.exe %UserProfile%\Desktop\FBI Moneypak Virus.lnk WARNING.txt V.class cconf.txt.enc tpl_0_c.exe irb700.exe dtresfflsceez.exe tpl_0_c.exe ch810.exe 0_0u_l.exe [random].exe
End ROGUE_NAME Processes:
Access Windows Task Manager (Ctrl+Alt+Delete) and kill the rogue FBI Moneypak process. Please note the infection will have a random name for the process [random] which may contain a sequence of numbers and letters (ie: USYHEY347H372.exe).
[random].exe
Remove Registry Values:
To access Window’s Registry Editor type regedit into the Windows Start Menu text field and press Enter.

HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\[random].exe HKEY_LOCAL_MACHINE\SOFTWARE\FBI Moneypak Virus HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Policies\System ‘DisableRegistryTools’ = 0 HKEY_LOCAL_MACHINE \SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system ‘EnableLUA’ = 0 HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Internet Settings ‘WarnOnHTTPSToHTTPRedirect’ = 0 HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Policies\System ‘DisableRegedit’= 0 HKEY_CURRENT_USER\Software\FBI Moneypak Virus HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run ‘Inspector’ HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\FBI Moneypak Virus HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Policies\System ‘DisableTaskMgr’ = 0 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Inspector %AppData%\Protector-[rnd].exe HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\WarnOnHTTPSToHTTPRedirect 0 HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\ID 4 HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\UID [rnd] HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\net [date of installation] HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorAdmin 0 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorUser 0 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA 0 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\Debugger svchost.exe HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\Debugger svchost.exe HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE\Debugger svchost.exe HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableRegistryTools” = 0 HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableTaskMgr” = 0 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “ConsentPromptBehaviorAdmin” = 0 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “ConsentPromptBehaviorUser” = 0 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “EnableLUA” = 0
System Restore – Recovery
Below we detail 3 different instructions to restore or recover a common Window’s computer.
Windows Start Menu Rstrui.exe Restore
- Access Windows Start menu
- Type rstrui.exe into the search field and press Enter
- Follow instructions in Window’s Restore Wizard
Start Menu Restore
- Access Windows Start menu and click All Programs.
- Click and open Accessories, click System Tools, and then click System Restore. If you are prompted for an administrator password or confirmation, type the password or provide confirmation.
- Follow the simple instructions to Restore your computer to a date and time before infection.
Safe Mode With Command Prompt Restore
If you can not access Window’s desktop, this is the suggested step. If it is difficult to start windows in safe mode; if Windows’s brings up a black screen, with “safe mode” in the four corners – Move your cursor to the lower left corner, where the Search box is usually visible in Windows Start Menu and it will come up, including the “Run” box.
1. Restart/reboot your computer system. Unplug if necessary.
2. Enter your computer in “safe mode with command prompt”. To properly enter safe mode, repeatedly press F8 upon the opening of the boot menu.
3. Once the Command Prompt appears you only have few seconds to type “explorer” and hit Enter. If you fail to do so within 2-3 seconds, the FBI MoneyPak ransomware virus will not allow you to type anymore.
4. Once Windows Explorer shows up browse to:
- Win XP: C:\windows\system32\restore\rstrui.exe and press Enter
- Win Vista/Seven: C:\windows\system32\rstrui.exe and press Enter
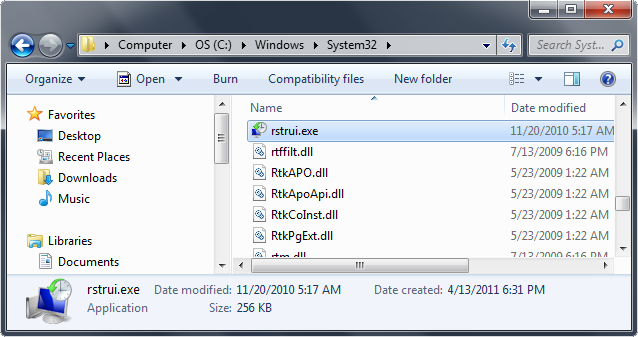
5. Follow all steps to restore or recover your computer system to an earlier time and date (restore point), before infection.
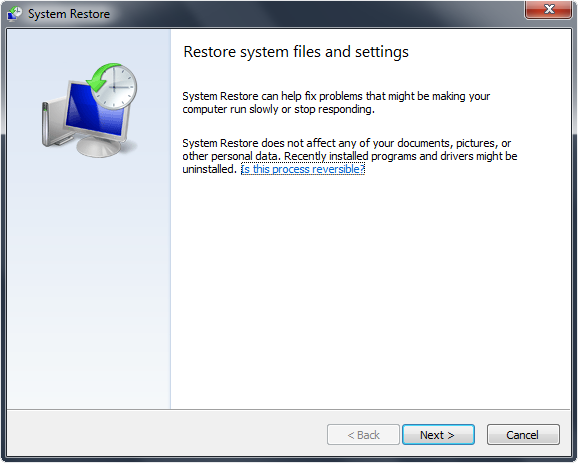
Safe Mode with Networking
For users needing access to the Internet or the network they’re connected to. This mode is helpful for when you need to be in Safe Mode to troubleshoot but also need access to the Internet for updates, drivers, removal software, or other files to help troubleshoot your issue.
- This mode will also bypass any issues where Antivirus or Anti Malare applications have been affected/malfunctioning because of the FBI Moneypak infection’s progression.
The plan with this option is to enter your computer in “safe mode with network” and install anti-malware software. Proceed to scan, and remove malicious files.
1. Reboot your computer in “Safe Mode with Networking”. As the computer is booting (when it reaches the manufacture’s logo) tap and hold the “F8 key” continuously to reach the correct menu. On the Advanced Boot Options screen, use your keyboard to navigate to “Safe Mode with Networking” and press Enter. Shown below.
- Make sure to log into an account with administrator rights.
The screen may appear black with the words “safe mode” in all four corners. Click your mouse where windows start menu is to bring up necessary browsing.

2. There are a few different things you can do…
- Pull-up the Start menu, enter All Programs and access the StartUp folder.
- Remove “ctfmon” link (or similar).
This seems to be an easy step in removing the FBI virus for many users. If you are interested in learning about ctfmon.exe please click here.
Now, move on to the next steps (which is not a necessity if you removed the file above but provides separate options for troubleshooting).
3. If you still can’t access the Internet after restarting in safe mode, try resetting your Internet Explorer proxy settings. These 2 separate options and following steps will reset the proxy settings in the Windows registry so that you can access the Internet again.
How To Reset Internet Explorer Proxy Settings
- Option 1
In Windows 7 click the Start button. In the search box type run and in the list of results click Run.
In Windows Vista click the Start button and then click Run.
In Windows XP click Start and then click Run.
Copy and paste or type the following text in the Open box in the Run dialog box and click OK:
reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings" /v ProxyEnable /t REG_DWORD /d 0 /f
In Windows 7 click the Start button. In the search box type run and in the list of results click Run.
In Windows Vista click the Start button and then click Run.
In Windows XP click Start and then click Run.
Copy and paste or type the following text in the Open box in the Run dialog box and click OK:
reg delete "HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings" /v ProxyServer /f
Restart Internet Explorer and then follow the steps listed previously to run the scanner
- Option 2
Launch Internet Explorer. In Internet Explorer go to: Tools->Internet Options->Connections tab.
Click Lan Settings button and uncheck the checkbox labeled Use a proxy server for your LAN. Click OK.
4. It is now recommended to download Malwarebytes (free or paid version) and run a full system scan to remove FBI Moneypak malware from your computer if you do not have this application on your system.
Flash Drive
- Turn off your computer system and Unplug your internet connection
- Turn the machine back on (In some cases the virus can only open if your machine is plugged into the internet)
- On another (clean) computer, download Malwarebytes or your preferred removal program and load the Mbam-Setup.exe (or similar) file onto the flash drive
- Remove the flash drive from the clean computer and insert it into the affected machine, proceed to install Malwarebytes (etc) using the setup file located on the flash drive.
- Run a full system scan, Malwarebytes will find and eradicate malicious files
- Restart your machine
Optical CD-R
- Place a blank CD-R into your CDROM drive
- Download and place Microsoft Defender or your prefered removal program onto the blank CD-R
- Restart your computer and boot from CD
“You may need an old school keyboard (not the USB, but the PC connector type) since the virus delays the USB startup. The Defender will clean your PC in totality. This virus is somehow complex, but is no match for Windows Defender. After the scan is complete, run again a full scan without a restart.”
Slave Hard Disk Drive
If you are having complications with Anti-Malware software a suggestion would be to slave your HDD, then proceed to scan. You will need a second operating computer and tools to remove your hard drive. *Please note this may be difficult for some users and there are other options to scan your hard drive during complications. This is a common practice for local computer technicians.
- Remove the Hard Disk Drive from your computer.
- On the circuit board side of your HDD set the drive to “slave”.
- Connect the slave drive to an unaffected computer.
- Scan the slave drive, and proceed to remove any malware on the drive. Make sure to scan each user account.
- Reconnect the HDD to your original computer.
The key to staying protected against future infections is to follow common online guidelines and take advantage of reputable Antivirus and Anti-Malware security software with real-time protection.
Real-time security software
Security software like Malwarebytes and Norton Security have real-time features that can block malicious files before they spread across your computer. These programs bundled together can establish a wall between your computer and cyber criminals.
- Backup your computer and personal files to an external drive or online backup service
- Create a restore point on your computer in case you need to restore your computer to a date before infection
- Avoid downloading and installing apps, browser extensions, and programs you are not familiar with
- Avoid downloading and installing apps, browser extensions, and programs from websites you are not familiar with – some websites use their own download manager to bundle additional programs with the initial download
- If you plan to download and install freeware, open source software, or shareware make sure to be alert when you install the object and read all the instructions presented by the download manager
- Avoid torrents and P2P clients
- Do not open email messages from senders you do not know





























I knew it was a virus. It was weird I was able to use the internet for like a few minutes each time I unplugged it. So I bought Malware Bytes instead of using the free one just so I could contact their support if thats how it wwent but it found the fbi virus right away. I didn’t even press scan.
Thank you! 🙂
I was literally about to drown myself in my own tears!
As you can tell I have been a victim of this awful scam and I want to thank you so much for being incredibly helpful with your multiple step-by-step instructions! It definitely took me many attempts to successfully remove the scam but nevertheless, I did it, all thanks to you! Thank you!!!
Remember, you can sue FBI if they did web-policing to violate your privacy.
My simple way to fix it:
enter safe-mode with networking.
Pull-up “Start” menu and “All Programs” “StartUp” folder.
Remove “ctfmon” link (or similar).
Thanks!
Thank you, thank you, thank you! I turned on my computer this morning and my computer was blocked, and I was freaking out that I was going to have to pay $200. Thanks for the help.
In my case it didn’t let me enter safe mode, it just freezed when all the list of drivers appear loading. But I found that if I opened a program like Advanced System Care or CCleaner (that asks you if you let them make changes in the computer) fast enough the blocking page didn’t appear. So I opened them and avast at the same time and programmed a virus scan when rebooting. The first time after the scan the blocking page showed again, but after a second reboot it said deo0_sar.exe couldn’t start because it was a virus. I think its over now.
Malwarebytes worked like a champ!
how far back should i restore my pc …i did it for yesterday…is that good enough
Restore your computer to a date and time before it was affected with malware.
First of all, thanks for caring so much! I can’t believe you take the time to respond to individual troubles. Humanity exists! Haha. That being said, can you explain the registry editor process? I’m trying to enter the data in safe prompt mode, but not sure how to go about it. Do I create new values (string, binary, etc?) This is all Mandarin to me. I’m just proud I made it this far!
my sister has this virus and she rebooted her computer before she called me. Her keyboard is not being recognized now. Any ideas on this?
She should still be able to enter safe mode by tapping F8 during boot up.
Well that can be a few things, but should be easily or even randomly fixed (or configured). If she is using a wireless keyboard the FBI Moneypak virus is known to interrupt recognition. If this is the case plugin a USB keyboard and check your “devices” for configuration settings.
Sometimes, if you restart your computer but do have your keyboard plugged in it may cause your keyboard to malfunction as well.
Hope this helps. If not and you seek more assistance please send me an email with more information sean@botcrawl.com and I’ll provide you with proper details.
PLEASE READ!!
The FBI Moneypak Ransomware Virus… I just got this virus on my laptop. It holds your computer hostage insisting that you play a fine to the FBI via a MoneyPack order. This virus is very smart.. totally disables your Anti-Virus/spyware programs. This is a scam, please do not pay money to these jerks. Here’s a link to a website that helped me get rid of it on my PC (only trouble is, you wil have to use a different pc/netbook or whatever to get this info becasue your pc will no longer work). It also resulted in me having to do a complete system restore.
Here’s the link…. http://botcrawl.com/how-to-remove-the-fbi-moneypak-ransomware-virus-fake-fbi-malware-removal/
Seems to have worked… thanks… awesome info
Thank you for this useful information. Manual worked fine. Great to see someone combating these pirates. Please keep up the good work and know it is appreciated.
Was running scared for a minute there….digital hug man.
Freakin awesome !!!!!
How To Remove The FBI Moneypak Ransomware Virus – Fake FBI Malware Removal: http://t.co/MjIOG20k
This is the best, thank you. Google needs to make this the top result not second because other articles were just terrible.
Omg…I am so glad I found this page. Stupid virus wouldn’t let me do anything. I unplugged my Internet and went into safe mode. Restored my comp to an earlier date. It seems to have worked. Hopefully it’ll stay that way. Thanks for the info 🙂
“@Nocside: Check this shit out. Scared the fuck out of me. http://t.co/q1oKUg3U” is it real, cuz I just got it on m
Wow that was easy Thank youu!
Had the same virus mine was real tough to get rid of. Glad I found the information here. Mine would not let me open anything in safe mode. I had to keep hitting F8 and click on top and lower safe mode corners to get explorer up. Then when the explorer box came up you have only a few seconds to type explorer in the box. Remember even in safe mode you don’t have a lot of time because the virus starts back up and safe mode shuts down and goes to the virus screen. Malware did not get rid of it because after the scan I started my computer up and the virus was back. I had to start all over trying to explorer back up it took some time again so you have to have some patience not like me. I had to walk away and I got my wife to try and guess what she got to the explore screen with the restore system up. I don’t know if this is a new and harder version to get rid of. So I had to restore first then ran malware 2nd and last I ran my avira anti virus scan. So far the computer seems ok. The information on this site was great lucky I had a lap top so I could access the info. Thanks Again
Beware phones at Houting Computer are starting to ring with more, and more reports of the “FBI Moneypak Ransom virus” this one is very bad news. It can take control of both your camera and your microphone. And thats only the fun part. Read this link to learn more. But.. be warned, if infected, you are very unlikely to remove this one yourself, regardless of the instructions listed below.
http://botcrawl.com/how-to-remove-the-fbi-moneypak-ransomware-virus-fake-fbi-malware-removal/
This info was great, i cant belive it was so easy to remove. Could someone tell me when and where this virus originared, i red something bout europe but this scam is just beyond anything i have ever seen…
Also can they actually see you? I did not notice the camera at the begining… Or is simply your own stream?
Also unplugging your internet completely stops the virus from working.
Thanks for the help
I got rid of the virus using AVG 2012 Anti-Virus software, and by doing a system restore afterwards. I highly recommend AVG because it is very thorough when scanning and it is so easy to configure and use.
Thank you so much for this information it worked frist try! I have been at it all day with no luck found this site and your answer tried it and its gone thank you again!
Malwarebytes took care of this problem..
Malwarebytes actually got it for me
Thank you SO much for posting this, it was a great help in manually removing this POS
Thank you soooo much for this instructions, I removed it in Safe Mode. It was easy to follow all the steps and I removed everything that has virus installation date and time in temp files. It installed on my work comupter and I was freaking out … You saved my day!!!
Many many many many thanks to you! This was the freakiest virus every, with the webcam and all! Too obvious for any individual with a brain to fall for but a pain in the neck to get rid of. We are so grateful for the instructions, could have not gotten to a point to navigate to system restore without, you have saved the day!!!
Thank you so much you saved me money wish I could donate or somethin.
Whenever I go to delete/open the temp folder it says I cannot do so because it is open in another program 🙁
The manual removal in safe mode with networking is what worked for me. The removal of the second part was named differently, so I simply deleted everything from that day/time. Thanks a lot for this!
This was a great help. So far so good, seems to have gotten rid of it.
just had to deal with this stupid virus made IE crash (thank you microsoft for easy IE crashing) to get out of that window, (i pressed control alt tab when ie crashed,) i started to restart so i could enter safe mode, had the popup of are you sure you want to lose the work on these programs with the options restart anyway or cancel, realized my webcam had turned off and hunted down and destroyed the files with a prejudice…….
Booting into Safe Mode (Continually tap the F8 on boot up) will give you the option to “Restore your computer to an earlier time” as soon as Windows loads. I just did this and selected a date prior to the infection and the machine booted up after the restore without issue. Then, scanned with MalwareBytes and found nothing. Infection gone. I’m either upgrading MalwareBytes to the pay version or installing Microsoft Security Essentials.
Sorry i meant in all four corners.
Another way to remove the FBI MoneyPak virus is to use Malwarebytes Anti-Malware software. You can find it here Malwarebytes.org. Just make sure you do a “Full” system scan. It will take longer than a quick scan, but it will detect, and allow you to remove the trojan.ransom virus (FBI MoneyPak) virus.
ive got the virus now, and for me if i disable or disconnect the internet the virus doesnt run. This may help others who are having issues with the virus to at least let you get access to your computers settings. so far i have tried multiple virus scanners and malware scanners all have said they have deleted it, but as soon as i reboot and reconnect the internet the screen locks again. Good luck everyone, this one is mean. i hope this little bit of info help you to at least access your system to try and get rid of it. so again DISABLE YOUR INTERNET and you should(as i did) gain access to your systems the virus seems to require an active connection to lock you out.
Randy
Safe Mode With Networking is an excellent solution for such issues.
System restore in safe mode did the trick, thanks lots.
guys i was freaking out…almost paid but i calmed down and looked it up luckily haha tis worked for me. the system restore i mean.
Thanks so much I’ve been through 4 days of hell trying to get rid of this thing
TROLLOLOLOLOL #how2 remove FBI moneypack virus http://t.co/PqKNMIYE #extortion #virus #fbi #moneypack #citadel#malware
http://t.co/O0qU6hiY
I was able to just simply restore my computer to a time earlier in the the same day that I got this ransomeware. Thanks. I was glad that I didn’t need to follow the instructions above, as am not the most computer savvy, though it doesn’t seem to painful. Thanks again.
Free version of malwarebytes worked for me.
How To Remove The FBI Moneypak Ransomware Virus – Fake FBI Malware Removal http://t.co/2pkZ74AO via @Botcrawl
You are a life savor. Thank you so much for this write up!!!!!!