A new Android banking malware family named Sturnus is emerging as one of the most capable threats targeting mobile users, combining credential theft, message surveillance, financial fraud automation, and full device takeover. The Sturnus Android banking trojan is designed to read encrypted chats from WhatsApp, Telegram, and Signal, harvest banking logins, and let attackers remotely operate compromised phones as if they were holding the device in their hands.
The malware, analyzed by mobile security company ThreatFabric, is fully functional even though it appears to still be in development. Early campaigns are limited and targeted mostly at victims in Central and Southern Europe, but the level of sophistication in Sturnus indicates preparation for broader operations. The operators behind the Sturnus Android banking trojan have already configured it with overlay screens for region-specific banks, remote control modules, and powerful surveillance routines that break the privacy protections of encrypted messaging apps.
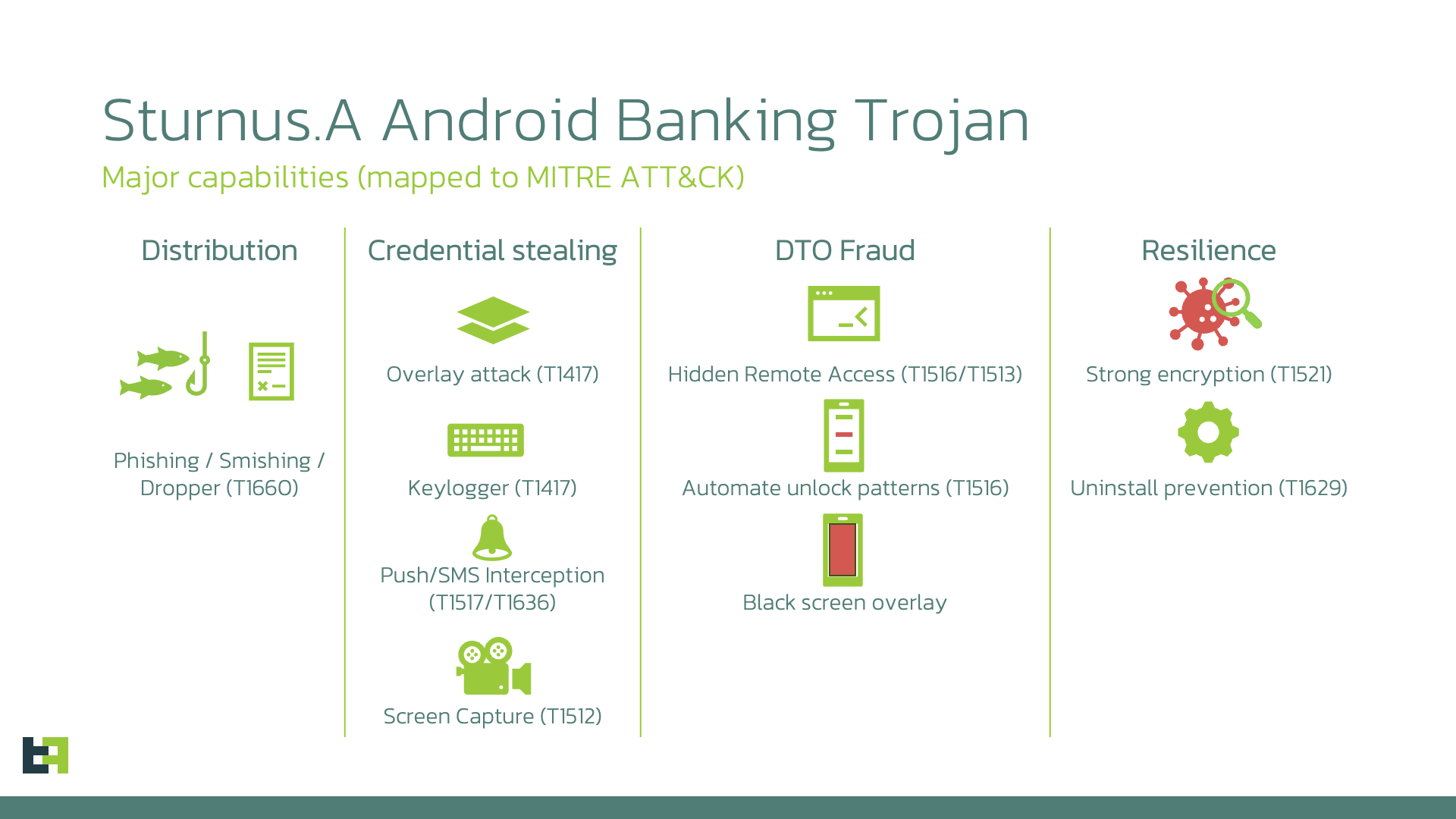
The malware infects devices through phishing, malicious app installers, and smishing links. Once installed, it immediately attempts to gain Android Device Administrator privileges. These privileges make Sturnus significantly harder to remove and allow it to intercept system events, block uninstall attempts, and monitor sensitive device activity. From this point forward, the device behaves as if it is fully exposed to the attacker.
Sturnus begins communication with its command server through a hybrid system that uses both WebSocket and HTTP channels. This design gives the operators real-time control while leaving a small detection footprint. After initiating contact, the server provides the malware with a unique identifier and an RSA public key. Sturnus generates a local AES key for further communication, encrypts it with RSA, and sends it back. All subsequent messages are encrypted with AES, making it difficult for network defenses to analyze command traffic.
Once communication is established, the Sturnus Android banking trojan activates its credential theft module. This module displays phishing overlays that imitate legitimate banking apps. When victims enter their username or password, the malware intercepts the data and forwards it to the operator. After the credentials are stolen, the overlay for that bank is disabled to avoid raising suspicion through repeated prompts.
Beyond overlays, Sturnus monitors system notifications and can intercept push messages and SMS codes used for two-factor authentication. Attackers can combine this information with remote control sessions to perform financial fraud. The malware includes a black screen feature that hides the device’s display with a full-screen overlay, allowing fraudulent activity to occur while the victim believes the device is idle or frozen.
One of the most concerning capabilities of Sturnus is its ability to bypass the protections of encrypted messaging apps. The malware monitors which application is currently open and activates a specialized routine whenever the victim launches WhatsApp, Telegram, or Signal. Because Sturnus relies on the Android Accessibility Service for data collection, it can read anything that appears on the screen in real time. This includes incoming and outgoing messages, contact names, conversation threads, and chat metadata. The encryption used by these messaging platforms does not prevent Sturnus from harvesting data because the malware captures content after it is decrypted by the legitimate app.
Alongside messaging surveillance, the Sturnus Android banking trojan maintains continuous awareness of the device environment. It tracks hardware information, connectivity changes, root detection signals, SIM transitions, power states, USB activity, developer settings, and installed applications. This helps the malware stay operational and avoid exposure inside emulator environments. The trojan also uses twelve internal broadcast receivers and a security thread to identify any signs of forensic investigation or removal attempts.
For remote operation, Sturnus uses two complementary layers. The first layer captures the device’s screen using either the Android display capture API or an accessibility-based screenshot fallback. This screen stream allows attackers to watch live activity and manipulate the phone as if they were physically interacting with it. The second layer uses structured UI-tree data instead of images. By analyzing the UI elements programmatically, attackers can trigger clicks, input text, scroll through screens, open applications, and accept permissions with minimal bandwidth usage. This approach remains functional even when screen capture attempts would normally be blocked.
Sturnus appears to be in a pre-deployment or testing phase, but its architecture and capabilities suggest that operators are preparing for a broader fraud campaign. Overlays mapped to region-specific banks in Central and Southern Europe indicate targeted victimology, and the monitoring of encrypted messaging apps suggests that attackers are exploring surveillance scenarios beyond traditional financial fraud.
The Sturnus Android banking trojan demonstrates the rapid evolution of mobile malware by blending credential theft, encrypted chat monitoring, remote control, administrator privilege abuse, and environmental awareness into a single threat. It also shows how attackers continue to exploit trusted device features such as accessibility services, notifications, and screen content to bypass app-level protections. As Sturnus continues to evolve, the combination of these capabilities represents a growing and highly flexible risk for Android users across multiple regions.



