A new threat actor cluster, tracked as CL-STA-1009, has been linked to the distribution of a sophisticated malware called Airstalk. According to research from Palo Alto Networks Unit 42, this backdoor misuses VMware AirWatch (now Workspace ONE Unified Endpoint Management) APIs to create a covert command-and-control (C2) channel. The attack is believed to be part of a suspected nation-state supply chain operation targeting business process outsourcing (BPO) firms and enterprise systems.
Table of Contents
- Overview
- How Airstalk Uses AirWatch APIs
- Airstalk PowerShell Variant
- Airstalk .NET Variant
- Core Capabilities and Commands
- Evasion and Signed Certificates
- Supply Chain and BPO Targeting
- Defensive Recommendations
Overview
Airstalk malware is available in both PowerShell and .NET variants, with the latter showing advanced development and additional capabilities. The malware abuses legitimate AirWatch mobile device management (MDM) APIs to communicate with command servers through normal enterprise traffic, helping it evade detection. Once installed, it can take screenshots, collect browser data, and exfiltrate sensitive information from Google Chrome, Microsoft Edge, and Island browsers.
Unit 42 discovered that some Airstalk samples are digitally signed using a stolen certificate issued to Aoteng Industrial Automation (Langfang) Co., Ltd., a legitimate Chinese company, suggesting a sophisticated and well-funded threat operation.
How Airstalk Uses AirWatch APIs
Airstalk’s most notable feature is its abuse of AirWatch MDM APIs for covert communication. Instead of using direct HTTP or DNS channels, it hides its traffic by embedding data within legitimate device management requests and responses.
The malware communicates with AirWatch servers using endpoints such as /api/mdm/devices/ and /api/mam/blobs/uploadblob, leveraging the custom attributes feature to store encoded JSON messages between infected systems and attacker-controlled servers.
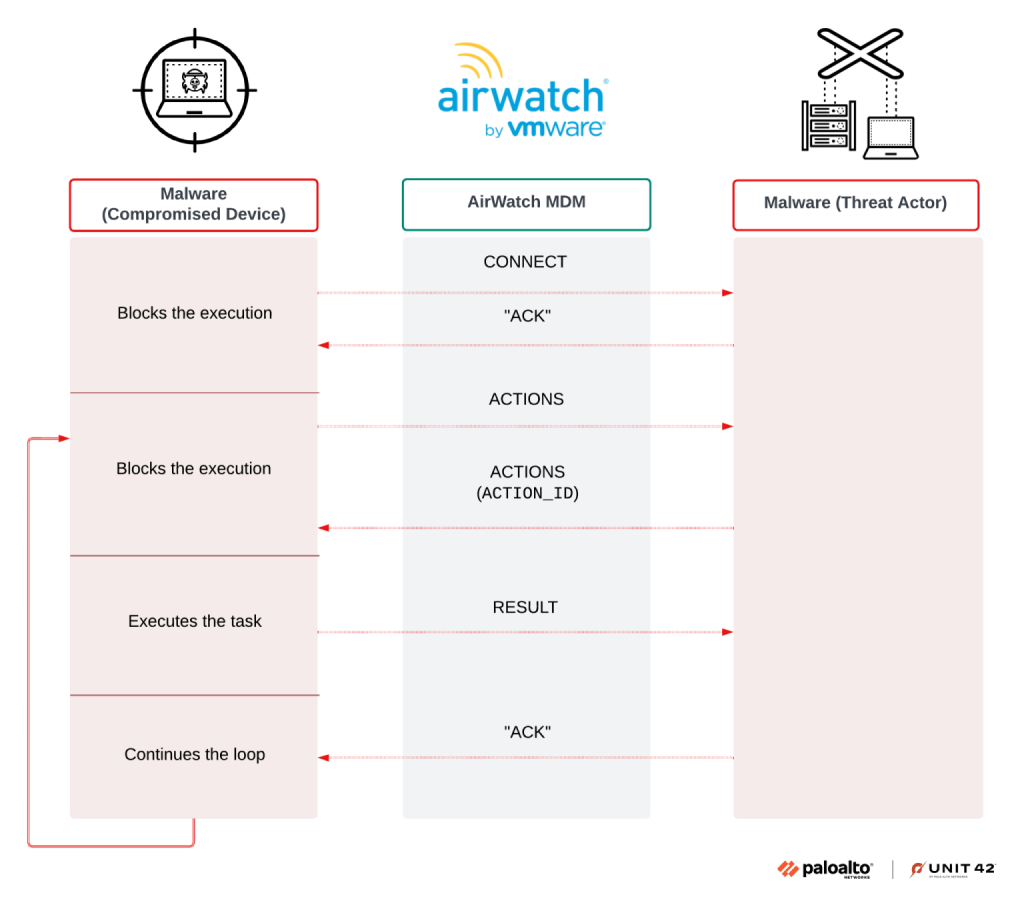
In this process, the compromised device continuously sends messages like CONNECT, ACTIONS, and RESULT through AirWatch’s legitimate API mechanisms. The attacker replies through the same channels, turning the MDM infrastructure into a hidden relay for malicious commands.
Airstalk PowerShell Variant
The PowerShell version of Airstalk uses a lightweight covert channel based on AirWatch device APIs. Once executed, it sends a CONNECT request to the server, waits for acknowledgment, and then exchanges ACTIONS and RESULT messages that dictate its behavior.
This variant can execute seven task types, including:
- Taking screenshots
- Dumping cookies from Chrome
- Listing user files and browser profiles
- Collecting bookmarks and browsing history
- Uninstalling itself
Data exfiltration occurs through AirWatch’s blob upload feature, which Airstalk uses to send large files such as screenshots or data archives without triggering normal network security alerts.
Airstalk .NET Variant
The .NET version of Airstalk is far more advanced. It mimics a legitimate AirWatch utility called AirWatchHelper.exe and expands its target list to include Chrome, Edge, and Island browsers. The malware supports a broader command set, multi-threaded execution, and a built-in debugging function that periodically uploads logs to the attacker.
The .NET variant introduces three new message types beyond the PowerShell version:
- MISMATCH – reports version conflicts
- DEBUG – transmits debug logs
- PING – performs regular beaconing
Its architecture uses three independent threads for continuous operation: one for managing C2 tasks, another for debug log exfiltration, and one for regular beaconing to maintain connection integrity.
Core Capabilities and Commands
The .NET version of Airstalk supports an extensive command library, with functions that allow it to capture screenshots, enumerate browser data, exfiltrate cookies and credentials, open URLs remotely, and uninstall itself. It can even retrieve lists of user profiles from both Chrome and Island browsers, helping attackers map enterprise activity.
Some commands remain unimplemented, suggesting ongoing development and modular expansion. The malware also includes a version variable, indicating structured version control and active updates.
Evasion and Signed Certificates
Researchers found that several Airstalk binaries were signed with a stolen certificate from a legitimate Chinese industrial company. The certificate was revoked shortly after issuance, but not before it was used to sign multiple Airstalk payloads, suggesting careful planning and testing by the attackers.
This signing tactic helps the malware bypass antivirus and malware detection mechanisms that rely on trust-based digital signatures. The PowerShell variant maintains persistence using scheduled tasks, while the .NET version operates only in memory without leaving traces, reducing its forensic footprint.
Supply Chain and BPO Targeting
Unit 42 assesses that Airstalk is likely used in a supply chain attack targeting organizations in the business process outsourcing (BPO) sector. Because BPO firms often manage customer data and have privileged access to client systems, they present a high-value target for both criminal and state-sponsored attackers.
By hiding within trusted vendor environments, Airstalk can steal browser session cookies, credentials, and screenshots from multiple organizations simultaneously. This creates a ripple effect, allowing attackers to compromise several enterprises through a single vendor network.
Defensive Recommendations
To protect against Airstalk malware and similar threats, organizations should:
- Ensure AirWatch and Workspace ONE APIs are not publicly exposed.
- Review logs for suspicious use of
/api/mdm/devices/and/api/mam/blobs/uploadblobendpoints. - Check for signed binaries associated with revoked certificates.
- Implement behavioral monitoring for unusual browser and PowerShell activity.
- Use reputable anti-malware and antivirus tools for defense in depth.
Because Airstalk can run within third-party vendor environments, visibility into external partners is critical. Enterprises should require security assessments from vendors with access to internal systems and monitor for anomalous AirWatch API activity across supply chain connections.
Conclusion
Airstalk represents an advanced evolution in how threat actors hide within legitimate management tools to bypass detection. Its misuse of enterprise MDM infrastructure and its ability to exfiltrate browser session data from within trusted environments make it particularly dangerous for corporate and government networks. As threat actors continue to exploit legitimate APIs for malicious control, the line between administrative traffic and malware communication grows thinner, demanding more intelligent, context-aware defense strategies.



Leave a Comment