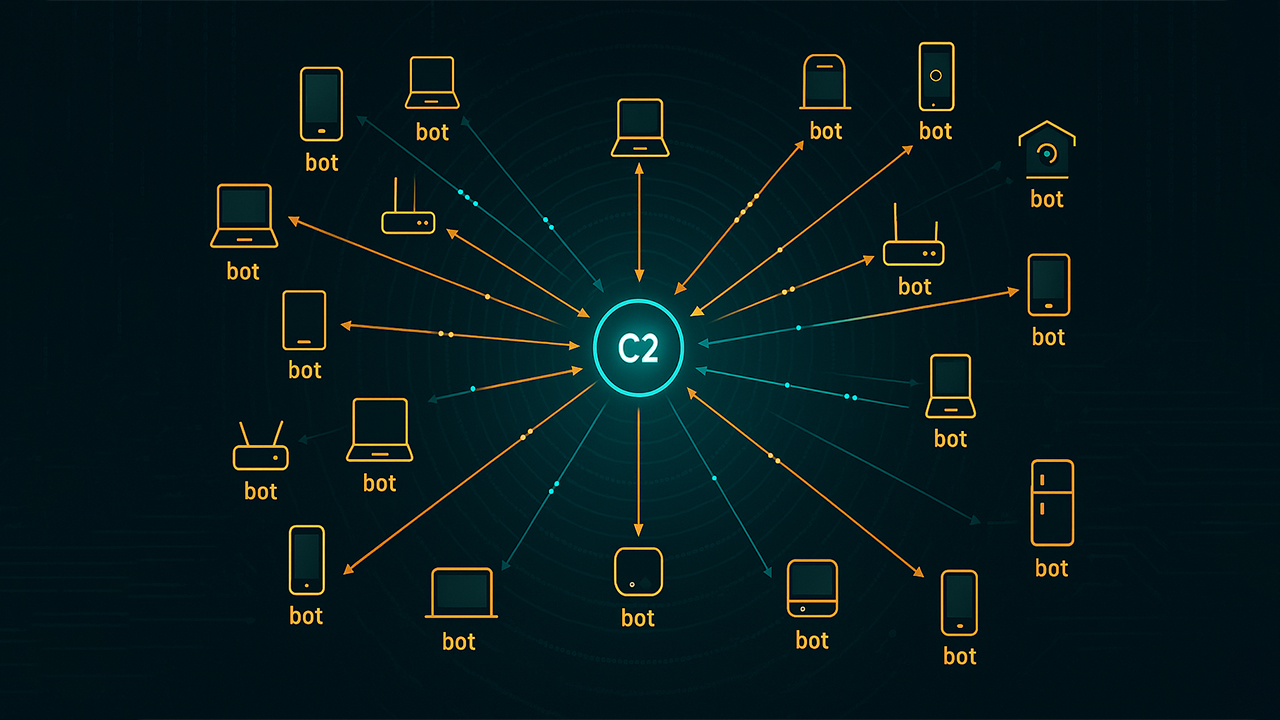
The RondoDox botnet is rapidly expanding its reach by weaponizing more than 50 vulnerabilities affecting over 30 technology vendors, according to new research. Security experts warn that the campaign, described as an “exploit shotgun,” is targeting routers, DVRs, CCTV systems, and other internet-exposed devices worldwide. Researchers say the malware is being distributed through a loader-as-a-service model, bundling RondoDox with Mirai and Morte payloads to launch massive distributed denial-of-service (DDoS) attacks and potentially enable data theft and persistent compromise.
Table of Contents
- What Is the RondoDox Botnet?
- How the New Campaign Works
- Affected Vendors and Vulnerabilities
- Connections to Other Botnets
- Expert Analysis and Warnings
- How to Protect Against RondoDox
- Key Takeaways
What Is the RondoDox Botnet?
The RondoDox botnet is a recently identified malware campaign that first surfaced in mid-2025. It was initially documented by Fortinet’s FortiGuard Labs after researchers observed attacks against TBK digital video recorders (DVRs) and Four-Faith routers. The botnet quickly drew attention because of its ability to exploit long-standing command injection flaws in internet-facing devices.
RondoDox is designed to compromise routers, network video recorders (NVRs), closed-circuit television (CCTV) systems, and other infrastructure connected directly to the internet. Once infected, devices are added to the botnet and used to perform distributed denial-of-service (DDoS) attacks, steal sensitive data, or deliver additional payloads.
Unlike traditional malware threats that focus on a single exploit or platform, RondoDox has demonstrated rapid adaptability. Researchers note that it uses a “shotgun” approach to compromise as many vulnerable devices as possible, often chaining together different exploits across various vendors.
How the New Campaign Works
Recent analysis from Trend Micro reveals that the RondoDox botnet has evolved far beyond its initial activity. The campaign now exploits more than 50 vulnerabilities across 30 different vendors, targeting routers, DVRs, NVRs, CCTV systems, and web servers. Researchers describe the method as an “exploit shotgun” approach, where multiple exploits are fired simultaneously at exposed devices in the hope that at least one will succeed.
One of the first observed intrusion attempts occurred on June 15, 2025, when attackers leveraged CVE-2023-1389, a well-known flaw in TP-Link Archer routers. This vulnerability, first disclosed in 2022, has been a frequent target of botnet operators and was previously used by campaigns linked to Mirai. By integrating it into its arsenal, RondoDox demonstrated its reliance on both newly discovered flaws and older vulnerabilities that remain unpatched on many devices.
Researchers also noted that RondoDox is distributed through a loader-as-a-service infrastructure. This means that compromised devices are not only infected with RondoDox itself, but also co-packaged with other malware such as Mirai and Morte. Once deployed, these payloads allow attackers to use the infected devices for:
- DDoS attacks: Launching large-scale denial-of-service campaigns using HTTP, UDP, and TCP traffic floods.
- Cryptomining: Installing miners to harvest cryptocurrency using the device’s processing power.
- Data exfiltration: Stealing sensitive information or credentials from compromised networks.
- Persistence: Maintaining long-term access to infrastructure for future exploitation.
This approach represents a significant evolution of automated exploitation. Instead of opportunistic attacks on a single product line, RondoDox now operates as a multivector loader operation, greatly expanding its potential impact across global networks.
Affected Vendors and Vulnerabilities
The latest RondoDox botnet campaign is notable for the sheer scale of its exploit arsenal. Security researchers have tracked at least 56 vulnerabilities being weaponized, spanning over 30 vendors. Out of these flaws, 38 have official CVE identifiers, while 18 remain unassigned. Most of the vulnerabilities are command injection flaws, but path traversal, buffer overflow, authentication bypass, and memory corruption issues are also present.
Vendors impacted by RondoDox exploitation attempts include:
- D-Link – multiple routers and NAS devices affected (e.g., CVE-2015-2051, CVE-2019-16920, CVE-2020-25506, CVE-2024-10914).
- TP-Link – Archer AX21 router flaw CVE-2023-1389, first disclosed at Pwn2Own, remains one of the most heavily exploited issues.
- Netgear – various models vulnerable to flaws such as CVE-2016-6277, CVE-2020-27867, and CVE-2023-51833.
- Apache – HTTP server path traversal vulnerabilities CVE-2021-41773 and CVE-2021-42013 are being abused in the wild.
- Four-Faith – industrial routers exploited via CVE-2024-12856.
- TBK – DVR products targeted with CVE-2024-3721.
- TOTOLINK – multiple router flaws, including CVE-2025-1829 and CVE-2025-5504, have been added to RondoDox payloads.
- Edimax – RE11S router vulnerable to CVE-2025-22905.
- QNAP – VioStor NVR impacted by CVE-2023-47565.
- Cisco – older product lines vulnerable to CVE-2019-1663, a memory corruption flaw.
- GNU Bash – Shellshock vulnerability CVE-2014-6271 still being recycled in attacks.
- Belkin – Play N750 router exploited via CVE-2014-1635 (buffer overflow).
- Zyxel – P660HN-T1A routers exploited through CVE-2017-18368.
Other affected vendors include TVT, LILIN, Fiberhome, Linksys, BYTEVALUE, ASMAX, Brickcom, IQrouter, Ricon, Nexxt, Meteobridge, Digiever, Dasan, LB-LINK, AVTECH, Hytec Inter, and Billion.
Researchers emphasize that a significant number of these vulnerabilities are already listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog. This means organizations should prioritize patching affected systems immediately, as active exploitation is confirmed worldwide.
Connections to Other Botnets
The RondoDox botnet is not operating in isolation. Researchers have uncovered clear overlaps between RondoDox and other well-known malware-driven botnets such as Mirai, Morte, and Aisuru. These links highlight how modern cybercriminal groups share infrastructure, payloads, and techniques to maximize impact.
Some of the most notable connections include:
- Mirai lineage: RondoDox uses many of the same exploitation tactics pioneered by the Mirai botnet. In several campaigns, researchers observed RondoDox payloads being packaged together with Mirai variants, effectively doubling the attack capacity of infected devices.
- Morte association: Trend Micro identified that RondoDox is distributed via a loader-as-a-service model, often bundled with Morte. This approach turns compromised routers and IoT devices into multipurpose attack nodes for DDoS and cryptomining operations.
- Aisuru overlap: Security journalist Brian Krebs has reported that Aisuru, one of the largest and most disruptive botnets active today, is also drawing significant firepower from compromised IoT devices. The infrastructure and infection patterns show overlap with RondoDox operations, suggesting shared operators or rented access to infected networks.
These interconnections show that RondoDox is part of a broader botnet ecosystem where groups recycle code, exploit toolkits, and infrastructure. This blending of capabilities makes detection and mitigation harder, as defenders may face simultaneous threats from multiple malware families operating on the same compromised device.
Security Implications and Mitigation
The widespread exploitation of over 50 vulnerabilities by the RondoDox botnet demonstrates how quickly attackers can weaponize known flaws in cybersecurity. Organizations that operate internet-facing infrastructure such as routers, DVRs, NVRs, and web servers are at heightened risk of compromise if they delay patching or fail to monitor their assets.
Unchecked infections can lead to:
- Data exfiltration – attackers may steal sensitive data or configuration files from compromised systems.
- Persistent compromise – once footholds are established, infected devices can be repeatedly exploited or resold to other threat actors.
- DDoS participation – compromised systems may be leveraged to launch massive distributed denial-of-service attacks against external targets.
- Cryptomining abuse – in some cases, RondoDox has been observed distributing miners alongside DDoS payloads, draining hardware resources.
Security experts recommend several mitigation steps to defend against RondoDox and similar botnet operations:
- Patch immediately: Prioritize vulnerabilities listed in CISA’s Known Exploited Vulnerabilities catalog, as they are confirmed to be actively targeted.
- Reduce internet exposure: Limit direct exposure of routers, NVRs, DVRs, and other edge devices whenever possible. Use VPNs and secure gateways instead of direct public access.
- Segment networks: Isolate critical systems from consumer-grade IoT devices to prevent lateral movement inside the network.
- Enforce strong credentials: Replace default passwords on all devices and enforce complex, unique credentials.
- Monitor continuously: Deploy intrusion detection and monitoring solutions to spot unusual traffic patterns, such as outbound DDoS participation.
- Conduct regular vulnerability assessments: Perform scans to identify outdated firmware, unpatched devices, or misconfigured endpoints before attackers exploit them.
Ultimately, the RondoDox campaign highlights the urgent need for proactive defense. Even flaws disclosed years ago, such as CVE-2014-6271 (Shellshock), are still being recycled in botnet operations. Organizations that delay patching or ignore older vulnerabilities create lasting opportunities for botnets to grow and evolve.
Key Takeaways
- The RondoDox botnet is actively exploiting more than 50 vulnerabilities across 30+ vendors, targeting routers, DVRs, NVRs, CCTV systems, and web servers.
- It uses a “shotgun” exploitation approach, chaining multiple flaws to compromise as many internet-exposed devices as possible.
- RondoDox is linked to other major botnets such as Mirai, Morte, and Aisuru, showing how cybercriminal groups share infrastructure and payloads.
- Infected devices are leveraged for distributed denial-of-service (DDoS) attacks, cryptomining, and persistent network compromise.
- Organizations must act quickly by patching vulnerabilities, enforcing strong passwords, segmenting networks, and monitoring for unusual traffic to reduce risk.
- Even older flaws, including some disclosed years ago, remain highly attractive to attackers when devices are left unpatched and exposed.


Leave a Comment