ProW File Compressor is a potentially unwanted program (PUP) that many people also call the ProW File Compressor virus. The word virus is used here because of how this program typically arrives on a device and how it behaves when paired with adware and browser hijackers. In theory, a file compression utility is simple and harmless. In practice, ProW File Compressor is rarely installed by choice. It rides along with software bundles, trojan downloaders, and deceptive installers that hide additional programs behind prechecked options or vague prompts. The result is a system that feels slower, a browser that changes unexpectedly, and a user experience shaped by third parties who profit from redirects and advertising rather than by your preferences. Security tools such as Malwarebytes commonly detect ProW File Compressor as a PUP. The components that deliver it, such as trojan downloaders and aggressive bundle managers, are often detected as outright malware.
This removal guide explains exactly what ProW File Compressor is, why it is considered unsafe, how it spreads, and how to remove it completely. You will learn how to identify symptoms, clean Windows and all major browsers, check for persistence mechanisms, and scan with Malwarebytes to catch hidden files and related PUPs. The goal is to restore control over your device and prevent a repeat infection. The instructions are written for a general Windows user, but power users will also find advanced steps that close common gaps left by basic cleanup.
What Is ProW File Compressor?
ProW File Compressor is presented as a desktop utility that compresses files to save disk space and improve transfer times. That pitch has surface credibility because compression tools exist and are widely used in business and research. A legitimate compression tool is easy to identify. It lives on a clear publisher site, is distributed through trusted stores, and is installed only when the user chooses it. ProW File Compressor does not fit that pattern in most cases reported by everyday users. Instead, it shows up after someone installs an unrelated program or clicks through a generic installer that promises speed and convenience. The person expects one product but gets a package.
This dual identity is why security analysts classify ProW File Compressor as a PUP. The executable itself may not exploit vulnerabilities or encrypt files. The harm originates in how it is delivered and in the company it keeps. Bundled ecosystems routinely add browser extensions with broad permissions, helper tasks that run at startup, and search intermediaries that reroute traffic through monetized endpoints. Over time, the system becomes noisier and less predictable. Even if a single binary looks ordinary, the total installation is not.
Antivirus tools reflect this reality. A traditional antivirus may not always flag the core ProW File Compressor executable in isolation. It will flag the components that install it, maintain it, and profit from it. Trojan downloaders are a prime example. Programs like Application Handsome are known to fetch additional payloads silently. A device that suddenly has ProW File Compressor also often has adware, toolbars, or browser policy entries that force specific search providers. In that context, the label ProW File Compressor virus is practical and fair. Users are not judging the code base. They are describing an experience where consent was bypassed and the outcome is unwanted.
How ProW File Compressor Gets Installed
Understanding distribution explains the risk. The typical user does not search for ProW File Compressor by name. Instead, it arrives through four common channels that share one goal. They maximize installs by minimizing real consent.
First is the bundled installer. Freeware portals and download mirrors often wrap legitimate software with their own installer framework. The user is offered shortcuts like Express or Recommended. Behind those options sit preselected offers. The copy is intentionally vague, and the interface encourages quick clicks. ProW File Compressor and several unrelated programs slide in during the same session. The uninstallers are separate, and some items do not appear immediately. Days later the user notices that search behavior changed or that extra utilities are present. That delay is part of the design.
Second is the trojan downloader. Malware such as Application Handsome presents as a helpful installer or update but runs code whose purpose is to reach a remote server, fetch payload lists, and drop executables in the background. There may be no visible prompt for the additional items at all. The person never chose ProW File Compressor, and yet it is present and active. That is a textbook example of an unwanted program and a common pattern behind the ProW File Compressor virus reports.
Third is unsafe advertising, also known as malvertising. Streaming portals, torrent indexes, and free file mirrors monetize through ad networks with weak standards. A click on a play button or a green Download badge may open a redirect chain. At the end of the chain is a generic download manager or a spoofed update prompt. The result is a handful of programs that install together. ProW File Compressor is a frequent passenger.
Fourth is the fake software manager. This class of tool claims to simplify installation and updates but is paid to deliver predetermined bundles. It may show checkboxes that appear optional while still installing the payloads. It may use a naming scheme that hides the true vendor. ProW File Compressor is seen in these flows along with search hijackers and surveyware.
All four channels share a property that matters more than any marketing text. The user’s choice is blurred. Consent is assumed where it was not given. That is the line between a useful utility and a PUP.
Why ProW File Compressor Is Considered Unsafe
ProW File Compressor is considered unsafe because it participates in an ecosystem that takes control away from the user and repurposes the device for advertising and tracking. The threat is cumulative. Each additional component amplifies friction and exposure.
Browser hijacking is the most visible symptom. Bundles that include ProW File Compressor often modify default search, homepage, and new tab settings. A query that previously went directly to a trusted engine now passes through one or more intermediaries. These pages log the request, attach identifiers, and monetize the traffic. Campaigns commonly route through hijackers similar to SearchWebPlus.com. The difference is immediately noticeable. The browser feels slower. The results page looks unfamiliar. Attempts to reset preferences may seem to work and then revert after a restart because a scheduled task or a policy key restores them.
Ad injection follows the same logic. Extensions included with the bundle request permissions that allow them to read and change data on all sites. That permission is enough to inject additional ad units into pages and to manipulate links so that more clicks become affiliate revenue. Some components also request notification access. Once granted, those alerts can bypass the browser and appear on the desktop even when the browser is closed. The volume increases over time because the system now resembles a billboard.
Privacy loss is built into this model. Each redirect and each injected element is an opportunity to capture browsing behavior. Partners in these ecosystems often harvest user agent strings, installed application lists, page visit sequences, broad location, and coarse device identifiers. The data is stitched together into profiles that guide ad targeting and partner payouts. Even if the ProW File Compressor executable makes no outbound connections, the partners that installed it and sustain it do. That is the operational definition of a PUP environment.
Persistence is the last problem and the reason that simple removal often fails. Tasks in Task Scheduler can relaunch helper processes at set intervals. Services can start automatically and reapply policy keys. Startup entries can recreate changed settings. A user who removes a suspicious extension on Monday may find it back on Wednesday because the root cause was never addressed. That persistence is intentional. It keeps the revenue stream alive.
Common Symptoms You May Notice
People often discover the ProW File Compressor virus by symptoms rather than by name. The patterns are consistent across machines because the business model is consistent across campaigns.
Search behavior changes first. You type a query and watch it detour through unfamiliar pages. The results still appear on a mainstream engine, but the journey is longer and the page is framed by extra ads. The default search setting refuses to stick. Each time you reset it, something switches it back.
The homepage and new tab page follow the same pattern. You set a trusted page. It reverts to a portal you did not choose. Some portals imitate real providers. Others are generic skins whose sole function is to route traffic.
New extensions appear in the browser with names that sound like helpers or safe browsing tools. They have broad permissions. You did not install them deliberately. When you remove them, they return after a reboot.
Advertising pressure increases. Sites that used to be quiet now show banners at the top and bottom and interstitials that cover content. Pop ups look like system alerts and nag you to click Allow to continue. If you allow notifications, the desktop fills with offers even when the browser is closed.
Windows shows unfamiliar entries in Installed apps or Programs and Features. The install dates cluster around the day the symptoms began. There may be optimizers, shopping tools, downloader managers, and update assistants that were never part of your plan.
Performance degrades. Startup takes longer. The browser stutters on simple pages. The fan runs more often because helpers are active even when the user is idle. These are not random glitches. They are byproducts of the bundle that delivered ProW File Compressor.
Risks Tied to the ProW File Compressor Ecosystem
The risks fall into five categories that build on each other and explain why immediate removal is necessary.
Exposure to fraudulent pages. Redirect chains frequently land on fake prize pages, bogus surveys, and full screen scareware that claims infection and lists a phone number for support. These pages attempt to extract payment, remote access, or both. Any increase in redirection increases exposure to these traps.
Installation of additional PUPs and extensions. Once a system has accepted one bundle, it is easier for the network behind it to deliver more. It may ship a new set of offers a week later. Users report a steady accumulation of tools they never sought out. Each one adds more friction and more opportunities for data collection.
Privacy loss through partners. The ecosystem does not need to read your emails to extract value. It needs to track flows and attach identifiers. Small signals add up to profiles that predict behavior and improve monetization. Those profiles can be sold or shared without meaningful transparency.
Credential exposure. Some flows insert imitation login pages for webmail, social networks, or shopping sites. A session token or password captured during a moment of inattention costs more than any ad annoyance. It leads to account takeovers, spam, and secondary fraud.
Persistence that resists removal. When a bundle adds tasks and policies, it gains leverage over your settings. You remove an extension and it returns. You change the homepage and it reverts. Without a thorough cleanup that addresses the root mechanisms, the symptoms never stay gone.
These risks are the practical definition of unsafe. They explain why even a simple utility becomes part of a virus narrative when it arrives through deception.
Manual Removal: Windows and Browsers
The most reliable cleanup plan follows a specific order. Remove visible programs first so that fewer components interfere with later steps. Disable persistence mechanisms next so that changes stick. Reset browsers and clear site data to cut off notification spam. Then scan with a trusted antimalware tool to catch hidden pieces that manual steps miss. Work carefully and do not skip steps.
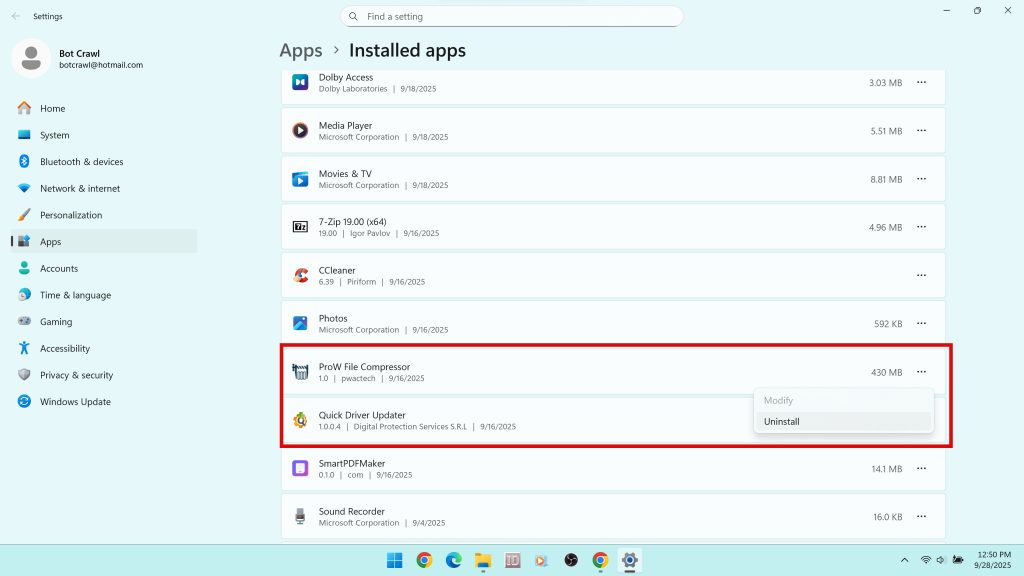
Begin with Windows program removal. Open Installed apps on Windows 11 or Apps and Features on Windows 10. Sort by Install date. Remove ProW File Compressor and any unfamiliar entries added on the same day. Pay attention to downloader managers, update helpers, optimizers, and anything with a vendor name you do not recognize. If an uninstaller fails or claims that a process is in use, reboot and try again. If the entry persists, proceed with the command line cleanup below.
Kill visible processes and remove the main folder and user level keys. The exact process name may vary by campaign. The following commands target the most common patterns.
taskkill /f /im prowfilecompressor.exe taskkill /f /im prowcompressor.exe reg delete "HKCU\Software\ProWFileCompressor" /f reg delete "HKLM\Software\ProWFileCompressor" /f reg delete "HKLM\Software\WOW6432Node\ProWFileCompressor" /f rd /s /q "C:\Program Files\ProWFileCompressor" rd /s /q "C:\Program Files (x86)\ProWFileCompressor"
Now disable persistence. Open Task Scheduler and look for tasks created around the install date that reference executables in AppData or ProgramData. Disable them first so they cannot relaunch, then delete them. Use Task Manager to disable unknown startup entries. If you prefer tools, launch Task Scheduler and System Configuration directly.
taskschd.msc msconfig
Reset browsers next. Remove unrecognized extensions and restore search, homepage, and new tab settings. Use the address bar shortcuts to reach each settings page directly.
Chrome extensions and reset pages:
chrome://extensions/ chrome://settings/search chrome://settings/onStartup chrome://policy chrome://settings/content/notifications
Edge extensions and reset pages:
edge://extensions/ edge://settings/search edge://settings/startHomeNTP edge://policy edge://settings/content/notifications
Firefox add ons and reset pages:
about:addons about:preferences#search about:preferences#home about:preferences#privacy
In each browser, remove extensions you did not install intentionally, especially ones with permission to read and change data on all websites. Reset search to your preferred engine and replace unfamiliar homepage or new tab URLs with a trusted default. Clear recent cookies and cached files. Revoke notification permissions for sites you do not recognize. This step alone reduces desktop spam that invites more redirects.
Finally, clean temporary folders that store leftover installers and caches. Open the following locations and delete visible items that are safe to remove.
%temp% temp
At this point, the visible pieces are gone and persistence is reduced. The next step confirms that no hidden components remain.
Scan for Adware, PUPs, and Hidden Components with Malwarebytes
Manual cleanup is important but it is not sufficient on its own. Bundles scatter components across user profile folders and registry locations that are easy to overlook. A thorough scan with a reputable tool is essential. Malwarebytes specializes in adware and PUP removal. It is effective at finding browser hijackers, notification spam engines, scheduled tasks tied to ad networks, policy entries that force search providers, and residual files linked to ProW File Compressor campaigns.
Use the following workflow for best results.
Download and install Malwarebytes: Click the button below and save the installer to your Downloads folder. The file name is usually MBSetup.exe.
Run the installer and allow updates: Double click MBSetup.exe. If Windows shows a User Account Control prompt, click Yes. Accept the license, keep the default path, and allow the program to update detection rules. Up to date definitions increase the chance of detecting the newest adware and hijacker variants.
Start a Threat Scan: Open Malwarebytes and click Scan. The Threat Scan examines memory, startup items, registry keys, scheduled tasks, and common hiding places used by PUPs and browser hijackers. This pass also identifies policy keys that force browser behavior.
Review results carefully: Expand each category to see detections. Typical items include adware DLLs, helper services, scheduled tasks named to resemble system processes, policy entries under Chrome or Edge that lock search settings, and leftover files in AppData folders. Look for references to ProW File Compressor or vendors you do not recognize.
Quarantine everything suspicious: Select all detected items and click Quarantine. Quarantine isolates files and registry changes so that they cannot run. This is safer than manual deletion for complex entries.
Reboot if prompted: A restart removes active components from memory and completes changes scheduled by the cleanup process.
Run a second Threat Scan: After reboot, open Malwarebytes again and run another scan. The second pass confirms that persistence mechanisms were disabled and that nothing reappears. A clean result here is a strong indicator that the system is stable.
If your browser continues to change or notification spam returns after a clean scan, check for managed browser policies you did not set. Chrome and Edge expose these pages to help with diagnosis. Remove the underlying program that set the policy and run another scan.
Chrome policy page:
chrome://policy
Edge policy page:
edge://policy
This combination of manual cleanup and targeted scanning resolves the vast majority of ProW File Compressor infections.
Advanced Checks When Problems Persist
Some installations leave artifacts that do not match the basic patterns. These checks help locate configuration changes that survive normal removal.
Shortcut targets. Right click your browser shortcut, choose Properties, and review the Target field. The command should end with the browser executable and nothing else. If a URL or an extra switch appears after the executable path, remove it. Example for Chrome:
"C:\Program Files\Google\Chrome\Application\chrome.exe"
Hosts file entries. Open the hosts file in Notepad and look for lines that redirect well known domains to unfamiliar IP addresses. If the entries are not yours, back up the file and remove the injected lines.
C:\Windows\System32\drivers\etc\hosts
Proxy settings. Unwanted proxies route traffic through filters that can alter pages or inject ads. Open Internet Options or the system proxy settings and disable any proxy you did not configure.
inetcpl.cpl
DNS configuration. Custom DNS can be helpful when set by the user. Unrecognized DNS can break lookups or route through monetized resolvers. Reset to automatic or set a trusted provider under your adapter properties.
ncpa.cpl
Scheduled tasks and services. If symptoms reappear on a schedule, a task is relaunching a helper process. Return to Task Scheduler and examine tasks that trigger at logon or every few minutes. Disable them first, then delete. In Services, look for entries created around the install date that reference unfamiliar vendors.
These checks close the gaps that bundles use to persist. Once complete, the device should behave normally and settings should stick.
Why Antivirus Sometimes Misses ProW File Compressor
A traditional antivirus engine focuses on code that exploits vulnerabilities, modifies system files directly, or exfiltrates data. PUP ecosystems operate a few steps away from those boundaries. They rely on social engineering, vague consent dialogs, and browser permissions instead of exploits. That is why the same program can be considered clean in one context and unsafe in another. The executable may not be flagged as malicious by signature. The distribution method and the surrounding components are the problem.
This leads to two patterns. The trojans, loaders, and fake managers that deliver ProW File Compressor are more likely to be detected as malware. The main utility may be allowed through by some engines. Users misread that as a green light. It is not. The right response is to remove the programs that arrived without clear consent and to scan with a tool that specializes in PUPs and adware. That is the niche where Malwarebytes performs well.
How to Avoid ProW File Compressor and Similar PUPs
Prevention relies on habits that reduce exposure to deceptive installers and unsafe networks. These steps are simple and effective when applied consistently.
Download software directly from the publisher site. Avoid mirrors and portal downloaders that wrap the installer with offers. When a site replaces the vendor’s installer with its own, assume additional items are included.
Choose custom installation every time it is offered. Deselect add ons, toolbars, shopping helpers, and recommended extras. If the installer hides choices behind vague summaries, cancel and find a cleaner source.
Be skeptical of generic download managers and update prompts. If a download starts from a site unrelated to the software you intended to get, close the tab and start over with a trusted source.
Use an ad blocker to reduce the number of deceptive landing pages presented by risky ad networks. This does not eliminate risk, but it removes a large portion of dangerous prompts.
Keep Windows and browsers updated. Built in protections are better at flagging uncommon downloads and unsafe installers when they are current.
Run periodic scans with Malwarebytes even when the system seems fine. PUPs are designed to look ordinary at first glance. A scan catches items that manual review misses.
Adopt the rule that anything installed without your explicit decision should be questioned. If a program appears and you did not seek it out, remove it and review the steps in this guide.
If You Already Opened Suspicious Files
If you executed an installer and then noticed the symptoms described here, complete the removal steps and take extra precautions. Assume that credentials used during the period of altered browsing may have been exposed.
Change passwords for important accounts, starting with email and financial providers. If a password manager stores your credentials in the browser, clear saved passwords and re authenticate only after the system is clean. Watch for sign in alerts that do not match your activity.
Enable multi factor authentication where available. A second factor limits the damage if a password was captured.
Review account recovery options and remove phone numbers or email addresses you do not recognize. Attackers who gain access sometimes change recovery paths to lock you out.
Check statements and transaction histories for charges you do not recognize. Credit card issuers and banks can reverse fraudulent activity when notified quickly.
These steps reduce the impact of any exposure during the period when a hijacker controlled the browser or when a trojan was active.
FAQ: ProW File Compressor Virus
Is ProW File Compressor a real virus? Not in the strict technical sense. It is commonly classified as a potentially unwanted program because of how it is distributed and what travels with it. People call it a virus because its arrival and effects feel like an infection.
Why did my antivirus not flag it? Some engines do not flag the main executable. They focus on trojans and exploit code. The delivery chain and partner components are the real risk. That is why scanning with Malwarebytes is recommended.
Can I keep ProW File Compressor if I like the compression feature? It is not wise. If it arrived through a bundler or a trojan, the environment that installed it remains a threat. Remove it and replace it with a trustworthy compression tool from a known publisher.
Will resetting my browser fix everything? It helps, but it does not remove scheduled tasks, services, or policy keys that reset your changes. Follow the full guide, then scan.
What if I use multiple browsers? Clean each one. PUP campaigns often target all installed browsers. Reset search and homepage settings, remove extensions, and revoke notifications in every browser you use.
Key Takeaways
ProW File Compressor is marketed as a compression utility, but it is widely distributed through bundlers, fake managers, unsafe ads, and trojan downloaders. That is why users refer to it as the ProW File Compressor virus. The risks include browser hijacking, ad injection, privacy loss, exposure to fraudulent pages, and persistence that resists casual removal. The most reliable fix is a layered approach. Uninstall suspicious programs, disable tasks and startup entries, reset browsers and revoke notifications, and then run a thorough scan with a tool that targets PUPs and adware. Once clean, adjust installation habits and stick to trusted sources so that the same ecosystem cannot take root again.
Download Malwarebytes to remove ProW File Compressor, adware, and PUPs:

Leave a Comment