The Ledger scam has become one of the most widespread threats facing cryptocurrency users today. Criminals are carrying out phishing campaigns that attempt to steal funds by tricking Ledger hardware wallet owners into revealing their 24-word recovery phrase. These attacks are designed to look convincing, often mimicking real Ledger emails, websites, or even customer support messages. However, they are always fraudulent and extremely dangerous.
Ledger has confirmed that it will never ask for your recovery phrase through email, text message, phone calls, or social media. The only place your recovery phrase should ever be entered is directly into your Ledger device. Falling for a Ledger scam can result in the permanent loss of all cryptocurrency stored in your wallet, making awareness and prevention critical.
In this article, we explain how Ledger scams work, show real examples of phishing emails, outline red flags to watch for, and provide steps you can take to protect yourself if you are targeted.
Table of Contents
- What Is the Ledger Scam?
- How the Ledger Scam Works
- Examples of Ledger Scam Emails
- How to Spot a Ledger Scam
- What To Do If You Fell for a Ledger Scam
- How to Stay Safe in the Future
- Key Takeaways
What Is the Ledger Scam?
The Ledger scam is a collection of phishing campaigns that target owners of Ledger hardware wallets. These scams are designed to look like official communications from Ledger but are in fact fraudulent attempts to steal cryptocurrency. The goal of every Ledger scam is the same: trick victims into revealing their 24-word recovery phrase. Once a scammer has this phrase, they gain full control of the wallet and its funds.
Ledger has made it clear that it will never ask for a user’s recovery phrase through email, phone calls, text messages, or social media. The only safe place to ever enter your recovery phrase is directly into the physical Ledger device. Any request to type the phrase into a computer, website, or application is a red flag that indicates a scam.
These scams appear in many forms, including fake emails, counterfeit Ledger Live applications, physical letters, scam NFTs, and social media impersonation accounts. Understanding how these scams operate is the first step in protecting yourself from becoming a victim.
How the Ledger Scam Works
The Ledger scam relies on a variety of phishing tactics. Each method is designed to look convincing and pressure the victim into sharing their recovery phrase or downloading malicious software. Once the recovery phrase is exposed, scammers can immediately take control of the wallet and steal its funds. Below are the most common tactics used in these scams.
- Fake Emails: Victims receive emails that appear to come from Ledger. These messages often claim that an “incident” or “security review” has taken place and instruct users to click a link to verify their account. The link leads to a fake website that asks for the 24-word recovery phrase. Once entered, the wallet is compromised.
- Counterfeit Ledger Live Apps and Websites: Scammers build fake applications and websites that closely mimic Ledger Live. Users are told to download these apps or log into websites that look legitimate but are actually controlled by attackers. Victims are then prompted to enter their recovery phrase under the pretense of fixing an error. The official Ledger Live app is only available at ledger.com/ledger-live.
- Phone Calls: Some scammers impersonate Ledger support agents over the phone. They may reference a legitimate support ticket opened in the victim’s name to sound more credible. Regardless of the excuse, Ledger has confirmed it will never contact users by phone.
- Physical Mail: In a rare but alarming twist, scammers have mailed letters to Ledger users. These letters often include a QR code or link to a website that requests the recovery phrase. Even if the letter looks professional, Ledger will never ask for such information through the mail.
- Scam NFTs: Attackers may send unsolicited NFTs to a user’s wallet. These NFTs typically claim that the user has won a prize or reward and provide instructions to claim it. Following the instructions usually leads to phishing websites. The safest response is to ignore and hide suspicious NFTs in Ledger Live.
- Fake Social Media Accounts: Fraudsters frequently create profiles on Twitter, Instagram, or Telegram that look like Ledger’s official accounts. They sometimes impersonate Ledger employees and message users directly, offering “support.” Any request for private information through social media is a scam, since Ledger does not provide customer service via direct message.
While these scams may look different on the surface, they all aim for the same outcome: gaining access to the recovery phrase. Once that phrase is in the wrong hands, the attacker has full control of the wallet and its contents.
Examples of Ledger Scam Emails
One of the most common forms of the Ledger scam is the phishing email. These messages are designed to look like official Ledger communications but are actually fraudulent attempts to steal your recovery phrase. They often use urgent or alarming subject lines, such as notifications of “security incidents” or “account verification.” Below are real examples of phishing emails that have been sent to Ledger users.
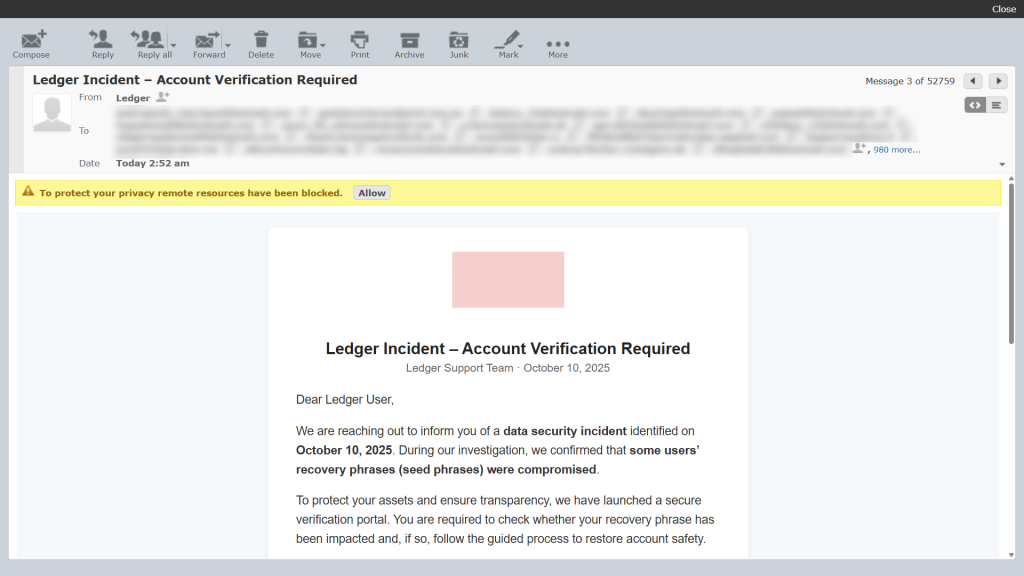
Subject: Ledger Incident – Account Verification Required
From: Ledger Support Team · October 10, 2025
Dear Ledger User,
We are reaching out to inform you of a data security incident identified on October 10, 2025. During our investigation, we confirmed that some users’ recovery phrases (seed phrases) were compromised.
To protect your assets and ensure transparency, we have launched a secure verification portal. You are required to check whether your recovery phrase has been impacted and, if so, follow the guided process to restore account safety.
What You Need to Do:
1. Click the button below to access our secure verification portal.
2. Check if your recovery phrase was compromised.
3. If affected, you will be automatically redirected to the regeneration and asset transfer portal for protection.
Verify My Account
The verification process is encrypted and secure. Ledger will never ask for your recovery phrase by email. If you receive any such request, please ignore it and report it to our support team immediately.
We sincerely apologize for the inconvenience this incident may have caused. Please verify your status as soon as possible to ensure your account remains protected.
Kind regards,
Ledger Support Team
Subject: Ledger Account Review Update Required
From: Ledger Support Notification · September 30, 2025
Dear Ledger User,
On September 30, 2025, our team completed a routine review of certain Ledger account data. During this process, we detected irregularities that may have affected a limited number of users.
To maintain the highest level of protection, we invite you to confirm your account information through our secure verification portal. This helps us ensure that your access credentials and phrase data remain accurate and protected.
Steps to Complete the Review:
1. Click the button below to access the secure verification page.
2. Follow the on-screen guidance to confirm your details.
3. If updates are required, the system will redirect you to finalize your account security setup.
Review My Ledger Account
This process is confidential and takes only a few moments. Please note that Ledger will never request sensitive information directly by email.
Thank you for your attention and continued trust.
Best regards,
Ledger Support Notification
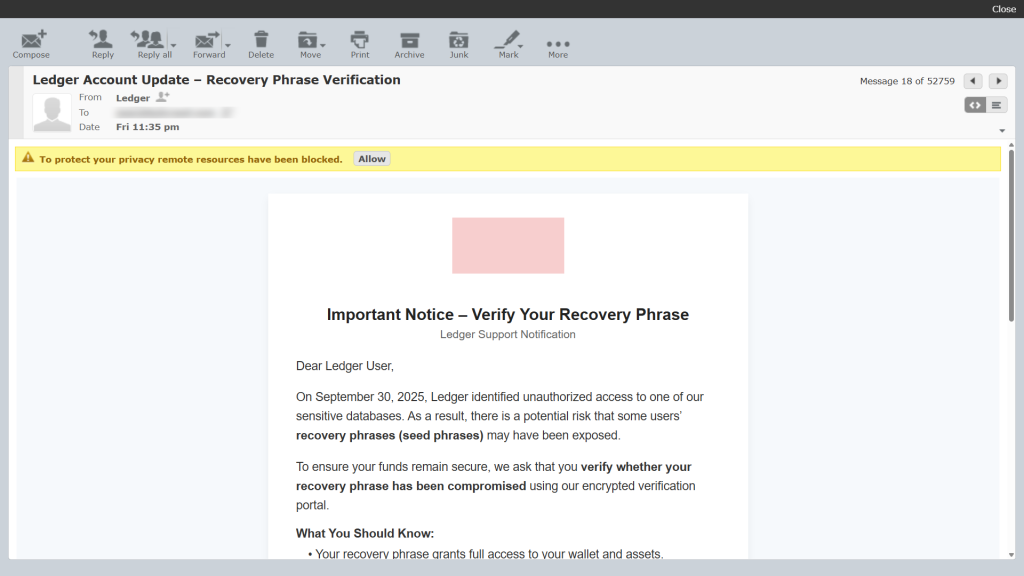
Subject: Ledger Account Update – Recovery Phrase Verification
From: Ledger Support Notification · September 30, 2025
Dear Ledger User,
On September 30, 2025, Ledger identified unauthorized access to one of our sensitive databases. As a result, there is a potential risk that some users’ recovery phrases (seed phrases) may have been exposed.
To ensure your funds remain secure, we ask that you verify whether your recovery phrase has been compromised using our encrypted verification portal.
What You Should Know:
• Your recovery phrase grants full access to your wallet and assets.
• If your phrase is compromised, you will automatically be redirected to our secure regeneration portal to create a new recovery phrase and safely transfer your assets.
• If your phrase is not affected, no further action is required.
How to Proceed:
1. Click the button below to open the secure verification portal.
2. Follow the on-screen steps to check the status of your recovery phrase.
3. If required, regenerate your recovery phrase and transfer your funds to a new wallet.
Verify My Recovery Phrase
This verification portal is encrypted and secure. Please remember: Ledger will never ask for your recovery phrase by email. If you receive such a request, ignore it and contact our support immediately.
We understand the seriousness of this situation and appreciate your prompt attention.
Sincerely,
Ledger Support Notification
As seen in these examples, the emails use urgency, alarming language, and fake portals to manipulate users. No matter how legitimate they look, remember that Ledger will never ask you to provide your recovery phrase through email or on any website.
How to Spot a Ledger Scam
Phishing messages connected to the Ledger scam are designed to look convincing. They often copy the design of official Ledger emails, websites, or apps, but there are always signs that reveal their fraudulent nature. By knowing what to look for, you can avoid falling victim to these scams.
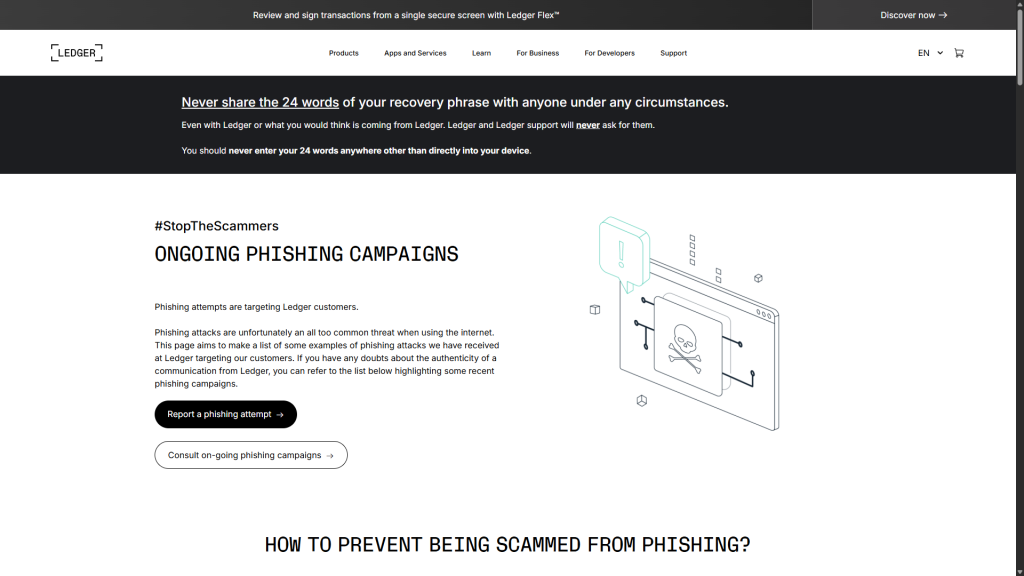
- Requests for your 24-word recovery phrase: This is the most obvious red flag. Ledger will never ask you to share your recovery phrase by email, phone, text message, website, or app. The only place it should ever be entered is directly into your physical Ledger device.
- Urgent or alarming subject lines: Phishing messages often use fear to push users into action. Subject lines like “Account Verification Required” or “Security Incident Detected” are designed to create panic and lower your guard.
- Unfamiliar or suspicious email domains: Official Ledger messages only come from addresses ending in
@ledger.com,@ledger.fr,@ledgerwallet.com, or@ledger.zendesk.com. Fake domains may look similar but contain subtle differences such as legder, leqder, or long, suspicious subdomains. - Unsolicited communication methods: Any message you receive from “Ledger” by phone call, SMS, WhatsApp, Telegram, or postal mail is fraudulent. Ledger does not contact customers through these channels.
- Fake social media support accounts: Attackers often impersonate Ledger or its employees on Twitter, Instagram, or Telegram. They may message you directly offering “help.” Ledger has confirmed it does not provide customer support through direct messages.
- Suspicious attachments or downloads: If you are prompted to download a new version of Ledger Live from anywhere other than the official Ledger website, it is a scam. Fake apps may look authentic but are designed to capture your recovery phrase.
By staying alert to these red flags, you can quickly identify a Ledger scam before it causes any damage. If you receive any communication that raises suspicion, stop immediately and verify the details on Ledger’s official website.
What To Do If You Fell for a Ledger Scam
If you entered your recovery phrase into a phishing website, app, or form connected to a Ledger scam, your wallet and funds are at immediate risk. Since cryptocurrency transactions are irreversible, it is critical to act quickly. Follow these steps as soon as possible:
- Create a new wallet: Set up a brand-new Ledger device or another secure wallet. This will generate a completely new 24-word recovery phrase. Do not reuse the compromised wallet, as attackers may still have access.
- Transfer your assets: Move all of your cryptocurrency from the compromised wallet into the new wallet you just created. Once funds are transferred, the old wallet should be abandoned.
- Stop using the compromised recovery phrase: Any account or wallet tied to that recovery phrase must be considered unsafe. Treat it as permanently compromised.
- Report the scam:
- Email the details to Ledger at phishing@ledger.fr.
- Report fake websites through Google Safe Browsing.
- Submit phishing attempts to the Federal Trade Commission if you are in the United States.
- Run a security scan: If you downloaded suspicious files or applications, run a full system scan with trusted Anti-Malware or Antivirus software to make sure your device is not infected with additional threats.
- Review your other accounts: If you reused passwords or had linked accounts, update your login credentials and enable two-factor authentication to prevent further compromise.
Acting immediately can reduce the damage caused by a Ledger scam. Even if some funds are lost, securing your other assets and reporting the scam helps protect both you and the broader cryptocurrency community.
How to Stay Safe in the Future
Staying ahead of phishing campaigns is the best way to avoid falling victim to a Ledger scam. Since scammers are constantly evolving their tactics, it is important to practice safe habits and always verify the source of any communication. The following steps will help protect your cryptocurrency and keep your Ledger device secure.
- Only use official sources: Always download Ledger Live directly from the official website at ledger.com/ledger-live. Do not trust links from emails, text messages, or social media posts.
- Never type your recovery phrase into a computer or website: The 24-word phrase should only ever be entered directly on your Ledger device. If any message, app, or site asks you to type it elsewhere, it is a scam.
- Check email addresses carefully: Official Ledger domains include
@ledger.com,@ledger.fr,@ledgerwallet.com, and@ledger.zendesk.com. Misspelled or unusual domains are a clear warning sign. - Ignore suspicious NFTs: Treat unsolicited NFTs as spam. Do not interact with them, and hide them in Ledger Live to avoid exposure to phishing links.
- Avoid unsolicited support contacts: Ledger will never contact you by phone, text message, WhatsApp, Telegram, or direct messages on social media. If you receive one of these, block and report the sender.
- Use strong cybersecurity practices: Protect your computer and mobile devices with updated antivirus software, enable automatic updates, and activate two-factor authentication wherever possible.
- Bookmark the official Ledger site: Save the real website in your browser bookmarks to avoid typosquatting domains that look similar to the official address.
- Stay informed: Ledger maintains an updated list of ongoing phishing campaigns. Regularly review their security alerts to keep up with the latest scam tactics.
By following these steps, you can significantly reduce the chances of being tricked by a Ledger scam and ensure your cryptocurrency remains safe under self-custody.
Key Takeaways
- The Ledger scam is a series of phishing campaigns that try to steal your 24-word recovery phrase through fake emails, apps, websites, letters, NFTs, and social media impersonations.
- Ledger will never ask for your recovery phrase by email, phone, text message, or social media. The only safe place to enter it is directly into your Ledger device.
- Common red flags include urgent subject lines, suspicious email domains, fake Ledger Live downloads, unsolicited phone calls, and direct messages from fake support accounts.
- If you fall victim, immediately create a new wallet, transfer your assets, abandon the compromised wallet, and report the scam to phishing@ledger.fr and relevant authorities.
- Prevention is key: use only official sources, keep your devices protected with updated antivirus and anti-malware tools, and stay informed about new phishing campaigns.
By recognizing the warning signs and following security best practices, you can protect your funds and avoid becoming another victim of the ongoing Ledger scam.


Leave a Comment