What Is The United States Cyber Security Virus?
The United States Cyber Security Virus (Cyber Security Virus, Fake U.S. Security Virus, U.S. DoD) is malware we discovered categorized as ransomware that locks computer systems and claims the computer user has been involved in illegal online activity by the FBI or other United States Cyber Security department such as the Department of Defense. The United States Cyber Security Virus claims the infected system either downloaded or distributed copyrighted material or viewed child pornography, among other extreme and mundane activities. The United States Cyber Security Virus then demands a penalty fine of $100 or $200 be paid to unlock the computer system by use of Moneypak cards and other online credit payment systems. The United States Cyber Security Ransomware Virus also states the infected user may see jail time if a fine is not paid. Please note, this computer virus is not associated with the actual United States government.

The infection disguises itself as the United States Cyber Security Department of Defense (or U.S. Department of Defense Cyber Command). This virus is not the actual United States Cyber Security department as preaviously mentioned (pictured below).
There are many ransomware viruses circulating the internet that are very similar to The United States Cyber Security ransomware virus. These ransomware infections include FBI Moneypak, Citadel Reveton, International Police, among others and are extremely dangerous (pictured below).
To learn more about other ransomware infections click here. To view our guide on ransomware removal click here. Please read further for The United States Cyber Security virus removal instructions.
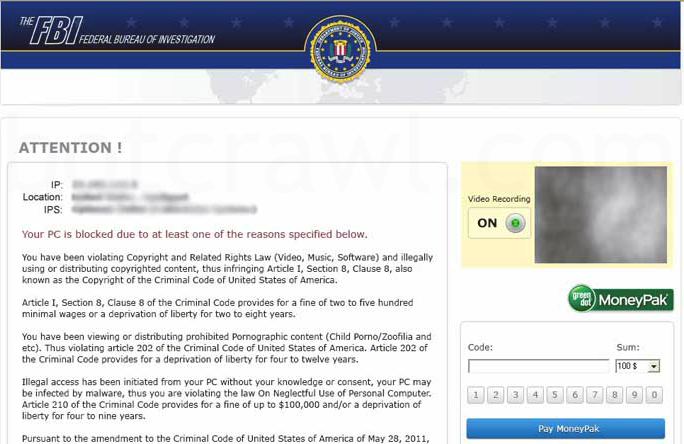
The United States Cyber Security Department Attention screen lock message:
Your pc is blocked due to at least one of the reasons specified below You have been violating Copyright and related rights Law (Video, Music,Software) and illegally using or distributing copyrighted content, thus infringing Article I, Section 8, clause 8, also known as the Copyright of the Criminal Code of United States of America. Article I, Section 8, Clause 8 of the Criminal Code provides for a fine of two to five hundred minimal wages or a deprivation of liberty for two to eight years. You have been blocked or locked as you have been viewing or distributing prohibited pornographic content(Child Porno/Zoofilia and etc). Thus violating article 202 of the Criminal Code of United States of America. Article 202 of the criminal provides for deprivation of liberty for two or twelve yours. Illegal access has been initiated from your PC without your knowledge or consent, your PC may be infected by malware, thus you are violating the law On Neglectful Use of personal Computer. Article 210 of the Criminal Code provides for a fine of up to $100,000 and/or a deprivation of liberty for four to nine years. Pursuant to the amendment to the Criminal of United States of America of May 28,2011, this law infringement (if it is not repeated – first time) may be considered as conditional in case you pay the fine to the state. Fines may only be paid within 24 hours after the infringement. As soon as 24 hours elapse, the possibility to pay the fine expires, and a criminal case is initiated against you automatically within the next 24 hours! To unlock the computer, you must pay the fine through MoneyPak of $200. To unlock your computer locked by the United States Cyber Security Moneypak Pay fine Virus and to avoid other legal consequences, you are obligated to pay a release fee of $200. Payable through GreenDot Moneypak via Walmart Card or Kmart Card etc. After successful payment, your computer will automatically unlock. How do i unlock computer using the MoneyPak? 1.Find a retail location near you. 2.Look for a MoneyPak in the prepaid section. Take it to the cashier and load it with cash. A service fee of up to $4.95 will apply. 3.To pay fine, you should enter the digits MoneyPak resulting code in the payment form and press Pay MoneyPak. When you pay the fine, your PC will get unlocked in 1 to 48 hours after the money is put into the state’s account. In case an error occurs, you’ll have to send the code by email fine@fbi.gov (Do not forget to specify IP address)
How To Remove The United States Cyber Security Ransomware Virus
There are a few different ways to remove The United States Cyber Security virus for individual infected users whom may have different variants of the particular ransomware infection. Therefore we have listed several options for each victim.
- Antivitus and Anti-Malware software is a simple way to scan for and remove ransomware infections (we’re not trying to push it on you, there are other options) and an easy way to ensure removal of the United States Cyber Security is effective after manual removal.
- Manually removing the U.S. Cyber Security ransomware virus may be a difficult process for many files will be identified randomly and computer systems may be too compromised to perform the removal process. When difficulties arise with manual removal, safe mode with networking is recommended to bypass any issue.
- Safe mode with networking is a process recommended by Microsoft to remove hijcker/ransomware viruses. Safe mode with networking can be used it a computer system can not be acecssed properly, nor can reach internet/network connection. Safe mode with networking allows you to bypass and access the internet for trouble shoot purposes, such as installing trouble shoot software, etc.
- A system restore will restore your computer to a date and time before the United States Cyber Security malware infection. *Window’s automatically creates restore points. This is a very easy removal process. For more information about system restores please click here.
The United States Cyber Security Virus Removal Options
- Antivirus/Anti-Malware Software – Scan and remove United States Cyber Security malware
- Manual Removal – Kill process, search for and remove directory files and registry entries.
- Safe Mode With Networking – Troubleshoot infected system
- System Restore – Restore computer to a date and time before infection. Click here for more info.
1. Antivirus/Anti-Malware Software
Your safest solution is to use Malwarebytes. Malwarebytes has the highest sample rate due to being the most downloaded Malware removal software in 2011 and 2012. They also provide free or paid versions and have been active in the removal of new ransomware viruses. Try Malwarebytes, the Leader in Malware Removal.
Other Antivirus Software Recommendations
AVG has recently been documented to scan and remove similar ransomware. They offer a free and paid version which they plan to keep updated. Please select one from the links below that suites your needs.
2. Manual Removal
Follow the steps below to manually remove The United States Cyber Security Ransomare Virus.
Kill ROGUE_NAME Processes:
Access Windows Task Manager (Ctrl+Alt+Delete) and kill the rogue FBI Moneypak process. Please note the infection will have a random name for the process [random] which may contain a sequence of numbers and letters (ie: Uj_93j.exe, check below).
[random].exe
We are going to enter your computers App Data (Application Data) which is a hidden folder with hidden files. To learn how to show hidden files click here.
1. Open Windows Start Menu and type %appdata% into the search field, press Enter.
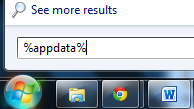
2. Navigate to: Microsoft\Windows\Start Menu\Programs\Startup
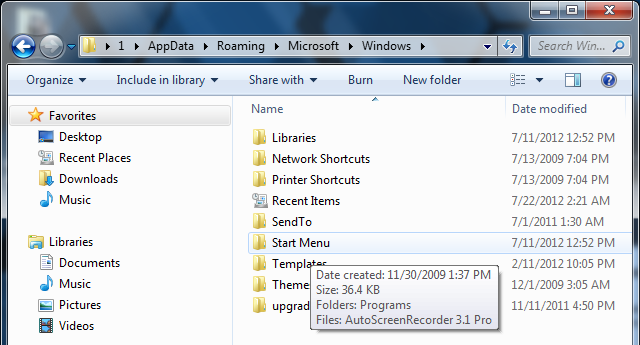
3. Remove ctfmon (ctfmon.lnk if in dos) – this is what’s calling the virus on start up. This is not ctfmon.exe.
(You can also find the infected ctfmon file here – C:\Users\[User]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ctfmon.lnk)
4. Open Windows Start Menu and type %userprofile% into the search field and press enter.

5. Navigate to: Appdata\Local\Temp
6. Remove rool0_pk.exe (Trojan.Ransom.Gen) and/or install_0_msi.exe (Trojan.PWS)

7.Remove [random].mof file
8. Remove V.class
The virus can have names other than “rool0_pk.exe” but it should appear similar, there may also be 2 files, 1 being a .mof. Removing the .exe file will fix common ransomware viruses. The class file uses a java vulnerability to install the virus, removal of V.class is done for safe measure.
The files listed above are what cause many Ransomare infections to function. Keep in mind, [random] can be any sequence of numbers or letters.
All The United States Cyber Security Ransomare Virus Files:
Remove all files and 1 documented folder.
C:\Program Files (x86)\FunWebProducts %Program Files%\[random] %AppData%\Protector-[rnd].exe %AppData%\Inspector-[rnd].exe %AppData%\vsdsrv32.exe %AppData%\result.db %AppData%\jork_0_typ_col.exe %appdata%\[random].exe %Temp%\0_0u_l.exe %Temp%\install_0_msi.exe %Temp%\rool0_pk.exe %Temp%\[random].exe %StartupFolder%\wpbt0.dll %StartupFolder%\ctfmon.lnk %StartupFolder%\ch810.exe WARNING.txt V.class cconf.txt.enc tpl_0_c.exe
Remove Registry Keys/Values
To access Window’s Registry Editor type regedit into the Windows Start Menu text field and press Enter.

HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{1D4DB7D2-6EC9-47A3-BD87-1E41684E07BB}
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\PreApproved\{1D4DB7D2-6EC9-47A3-BD87-1E41684E07BB}
HKCR\DOWNLOADER.DownloaderCtrl.1
HKCR\AppID\activex.DLL
HKLM\SOFTWARE\FunWebProducts
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\[random].exe
HKEY_LOCAL_MACHINE\SOFTWARE\UnitedStatesCyberSecurity
HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Policies\System ‘DisableRegistryTools’ = 0
HKEY_LOCAL_MACHINE \SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system ‘EnableLUA’ = 0
HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Internet Settings ‘WarnOnHTTPSToHTTPRedirect’ = 0
HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Policies\System ‘DisableRegedit’= 0
3. Safe Mode With Networking
1. Reboot your computer in “Safe Mode with Networking”. As the computer is booting (when it reaches the manufacture’s logo) tap and hold the “F8 key” continuously to reach the correct menu. On the Advanced Boot Options screen, use your keyboard to navigate to “Safe Mode with Networking” and press Enter. Shown below.
- Make sure to log into an account with administrator rights.
The screen may appear black with the words “safe mode” in all four corners. Click your mouse where windows start menu is to bring up necessary browsing.
2. There are a few different things you can do…
- Pull-up the Start menu, enter All Programs and access the StartUp folder.
- Remove “ctfmon” link (or similar).
This is sometimes a common file for ransomware viruses. If you are interested in learning about ctfmon.exe please click here.
Now, move on to the next steps (which is not a necessity if you removed the file above but provides separate options for troubleshooting).
3. If you still can’t access the Internet after restarting in safe mode, try resetting your Internet Explorer proxy settings. These 2 separate options and following steps will reset the proxy settings in the Windows registry so that you can access the Internet again.
How To Reset Internet Explorer Proxy Settings
Option 1
In Windows 7, click the Start button . In the search box, type run, and then, in the list of results, click Run.
-or-
In Windows Vista, click the Start button , and then click Run.
-or-
In Windows XP, click Start, and then click Run.
Copy and paste or type the following text in the Open box in the Run dialog box and click OK:
reg add “HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings” /v ProxyEnable /t REG_DWORD /d 0 /f
In Windows 7, click the Start button . In the search box, type run, and then, in the list of results, click Run.
-or-
In Windows Vista, click the Start button , and then click Run.
-or-
In Windows XP, click Start, and then click Run.
Copy and paste or type the following text in the Open box in the Run dialog box and click OK:
reg delete “HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings” /v ProxyServer /f
Restart Internet Explorer and then follow the steps listed previously to run the scanner
Option 2
Launch Internet Explorer. In Internet Explorer go to: Tools->Internet Options->Connections tab.
Click Lan Settings button and uncheck the checkbox labeled Use a proxy server for your LAN. Click OK.
4. It is now recommended to download Malwarebytes (free or paid version) and run a full system scan to remove US Cyber Security malware from your computer if you do not have this application on your system.







SHIT IT DING NOW
what if the virus is on my phone ?how will I be able to remove it.
I had this show up from the US Department of Defense saying i had to pay 450 dollars. I started freaking out thinking i did something wrong. Restoring my computer right now, hope it works
My question is if y’all know about it how come they haven’t found parties responsible and lock them up?
I removed this by (1) booting a UBCD disk then (2) deleting the flashapp files that were recently added to the windows/system32 folder. Rebooted and it was gone.
i got it last night, thankfully i happened to stumble onto this page while trying to research if or not it was a violation of rights. malwarebytes picked up over 40 files that avg missed! MANY THANKS to you, and to the security pro’s at malwarebytes.
BTW – I’m almost 100% postive I got it while downloading NFL Clipart. The last time I got a virus it was from Clipart as well. You just never know I guess
RT @botcrawl: How To Remove The United States Cyber Security Ransomare Virus (Us Security Virus) http://t.co/sKz1VCoB
thanks!
Ugh, now I can’t delete the file because: “The action can’t be completed because the file is open in Windows host process (Rundll32)” It also seemed to erase many settings (cookies?) from different websites.
Ctrl+Shit+Esc > Processes tab and kill it. Erasing cookies is fine, it’s actually good.
no, the Task Manager would not operate. Malwarebytes software fixed it all now. BTW, while it was scanning, it made 3 attempts at something outgoing. Trying to infect others I assume (iexplore).
iexplore.exe is a an Internet Explorer file as well as a very common name which many malware infectoins use. Most likely if a bugged process occurred, some sort of connection to the internet was trying to be accomplished.
My infestation prevented the task manager from working. I was only able to get to my desktop by forcing shutdown and quickly cancelling when it tried to shut down a background program.
I tried to manually remove the “ctfmon” program from my startup directory, but it replicates it as fast as I can delete it. The same happened with a c prompt. So then I followed the %userprofile% instructions above. I did not find any “rool” file, but I did find “install_0_msi.exe”. I’ll try to delete that then return to the %appdata% procedure above. I think I’ll go buy software.
If you do not want to purchase software, and without knowing the details of your issue, I suggest a system restore. Window’s automatically creates restore points. If you are unfamiliar, check it out!
I totally freaked out when I saw this virus in my computer. Now I will try to get rid of it with these instructions. Just one question… how did I possibly get it? I just connected with a new company hours before it showed up. The sites I visited were: google, facebook, google maps, amazing race site and I downloaded a Flayer Player update… I wish I could tell if the it was a fake update… I was in a hurry and did not make sure if it was truly from Adobe… 🙁 How do people get this virus? Thanks a lot for your answer and these instructions.
I can’t certainly diagnose where the infection was contracted or in what exact time table it occurred on your system but there are many infected websites around the internet which contain malware.
If that was your order of process (Google, FB, etc) while utilizing your new connection, the Flash Player update may be a red flag… though Adobe did release a new update on the 21st of August (version 11.4.402.265).
Thanks!
Restore was turned off. I can’t imagine I had it that way (but maybe I did). I assume it turned that off as well. It did all kinds of things.
Rarely have I noticed restore points being removed in association with ransomware.
Sometimes restore points are removed if a restore was successful or not completed correctly (in which Windows will notify you it was unsuccessful/not a human error).
If you want to discuss details in depth feel free to email me Sean@botcrawl.com
I would actually like to see your Malwarebytes log if you do not mind. It may help others.
How To Remove The United States Cyber Security Ransomare Virus (Us Security Virus) http://t.co/B4V7rgrE
Thank you so much! Youre the best!