What Is The Interpol Department Of Cybercrime Ransomware Virus?
 The Interpol Department Of Cybercrime virus (Interpol Virus) is ransomware controlled by the use of trojans that holds computer systems hostage and displays a fake Interpol screen which frightens computer users to suspect their computer was used in cybercrime such as child porn, zoofilia, and the Interpol virus will most likely state the computer was used to download or distribute video, music, and software against copyright and related rights laws in the country of Great Britain. The Internpol Department Of Cybercrime virus then demands a penalty fine to be paid either by Paypal, UKash, or Playsafecard in order to unlock and use the locked computer. Though this fake Interpol malware is likely to strike in Europe, users have been infected throughout other continents.
The Interpol Department Of Cybercrime virus (Interpol Virus) is ransomware controlled by the use of trojans that holds computer systems hostage and displays a fake Interpol screen which frightens computer users to suspect their computer was used in cybercrime such as child porn, zoofilia, and the Interpol virus will most likely state the computer was used to download or distribute video, music, and software against copyright and related rights laws in the country of Great Britain. The Internpol Department Of Cybercrime virus then demands a penalty fine to be paid either by Paypal, UKash, or Playsafecard in order to unlock and use the locked computer. Though this fake Interpol malware is likely to strike in Europe, users have been infected throughout other continents.
Similar ransomware: Citadel Reveton, FBI Moneypak, International Police Association (IPA)
Like most ransomware the fake Interpol virus creates files and registry entries which in turn will allow the infection to run itself every time the computer system is turned on. Luckily this article will describe options to remove this dangerous Interpol Department Of Cybercrime virus.

Interpol Department Of Cybercrime Ransomware Virus Symptoms
- The Interpol Department Of Cybercrime ransomware virus installs onto computer systems without permission.
- The Interpol Department Of Cybercrime ransomware virus is capable of hijacking, redirecting, and changing internet browser settings and installing other forms of malware such as adware and spyware. Infected users often have other bundles of malware.
- Once infected with the Interpol Department Of Cybercrime ransomware virus the computer system becomes locked. The computer user can not access the internet, nor properly navigate through their operating system.
- A fake Interpol website or screen states: “YOUR PC IS BLOCKED DUE TO AT LEAST ONE OF THE REASONS SPECIFIED BELOW”
- You have been violating Copyright and Related Rights Law (Video, Music, Software) and illegally using or distributing copyrighted content, thus infringing Article 128 of the Criminal Code of Great Britain. Article 128 of the Criminal Code provides for a fine of two to five hundred minimal wages or a deprivation of liberty for two to eight years.
- You have been viewing or distributing Pornographic content (Child Porn/Zoofilia etc.) This vilating article 202 of the Criminal Code of Greatb Britain. Article 202 of the Criminal Code provides for a deprivation of liberty for four to twelve years.
- Illegal access to computer data has been initiated from your PC, or you have been… (concludes the rest of the article)
- Article 208 of the Criminal Code provides for a fine up to €100,000 and/or a deprivation of liberty for four to nine years.
- Illegal access has been initiated from your PC wtihout yoour knowledge or constent, your PC may be infected by malware, thus you are violating the law of Neglectfil Use of Personal Computer. Article 210 of the Criminal Code provides for a fine of €2,000 to €8,000.
Web Cam Control
When the computer user is taken to the fake drive-by-download website or fake Interpol screen, a video connection, which is streamed from the users connected webcam is displayed as “recording”. If you do not have a web cam connected the video screen will appear blank and will still show as recording.
- You can stop your webcam stream against this virus by denying flash. To deny flash please click here.
How to remove the Interpol virus (Ransomware)
- Anti-Malware Software – Scan and remove Interpol malware.
- Manual Removal – Kill process, delete directory files, remove registry values.
- System Restore – Restore your computer to a date and time before infection.
- For Tech Support – Call 1-888-986-8411 and they will kindly assist you with removing this infection
1. Anti-Malware Software
1. We highly recommend writing down the toll free number below in case you run into any issues or problems while following the instructions. Our techs will kindly assist you with any problems.
if you need help give us a call
2. Install the free or paid version of Malwarebytes Anti-Malware.
3. Once Malwarebytes is installed, run the program. If you are using the free version of Malwarebytes you will be prompted to update the database, make sure to do so.
4. On the first tab labeled “Scanner” select the Perform full scan option and click the Scan button to perform a full system scan. Malwarebytes will automatically detect malware infecting the computer system.

5. Once the malware scan is complete, Malwarebytes may prompt a notice stating malicious objects were detected. Select the malicious objects and click the Remove Selected button to completely remove the malicious files from your computer (the image below shows a file that is NOT selected) or click the Delete button to remove files.

2. Interpol Virus Manual Removal Procedure
To manually remove fake Interpol malware please follow all outlined steps. First kill the malicious processes, then remove directory files created by the infection, and finally delete registry entries (values) created by the Interpol Department Of Cybercrime ransomware virus.
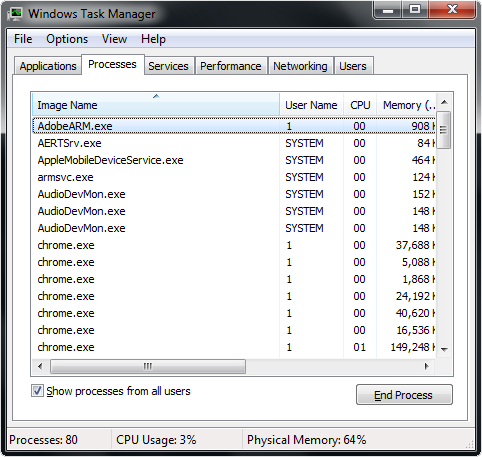
Kill Process
Launch the Task Manager by pressing keys “CTRL + Shift + ESC”
Select the “Processes” tab and search for both Interpol Department of Cybercrime Ransomware processes and right-click to end them.
- %System%\winlogin.exe
- %Windir%\winrun.exe
Remove Directory Files
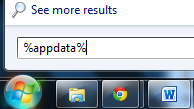
Click on Window’s “Start” menu and then click on the “Search programs and files” box and search for and delete the files created by Interpol Department of Cybercrime Ransomware:
You can also enter %AppData% into Window’s Start Menu search box and press enter to enter the Application Data folder which these files are located in.
- %AppData%\NPSWF32.dll
- %AppData%\random.exe
- %AppData%\result.db
Remove Registry Values
Open Registry Editor by navigating to Window’s “Start” Menu, and typing “Regedit” into the seach box then click “OK” to proceed.
When Window’s Registry Editor is open, search and remove of the following registry entries:
| HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Inspector %AppData%\random.exe | |
| HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\WarnOnHTTPSToHTTPRedirect 0 | |
| HKCU\Software\Microsoft\Windows\CurrentVersion\Settings\ID 4 | |
| HKCU\Software\Microsoft\Windows\CurrentVersion\Settings\UID [rnd] | |
| HKCU\Software\Microsoft\Windows\CurrentVersion\Settings\net [date of installation] | |
| HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorAdmin 0 | |
| HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorUser 0 | |
| HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA 0 | |
| HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe | |
| HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\Debugger svchost.exe | |
| HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe | |
| HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\Debugger svchost.exe | |
| HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE | |
| HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE\Debugger svchost.exe | |
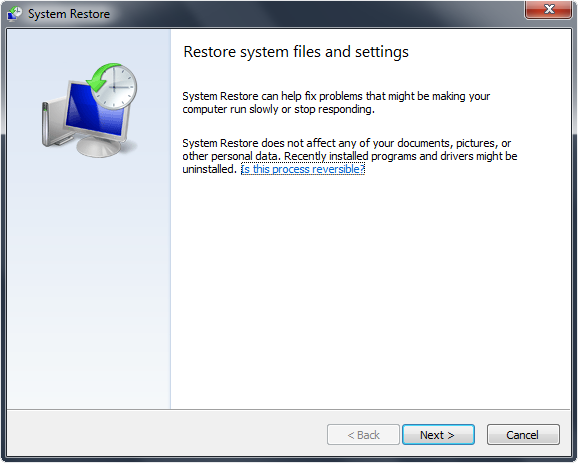
3. System Restore
Option 1: Windows Start Menu rstrui.exe Restore
1. Access Windows Start menu
2. Type rstrui.exe into the search field and press Enter
3. Follow instructions in Window’s Restore Wizard
Option 2: Windows Start Menu Restore
 Standard directions to quickly access Window’s System Restore Wizard.
Standard directions to quickly access Window’s System Restore Wizard.
1. Access windows Start menu and click All Programs.
2. Click and open Accessories, click System Tools, and then click System Restore.
If you are prompted for an administrator password or confirmation, type the password or provide confirmation.
3. Restore your computer to a date and time before infection.
Option 3: Windows Safe Mode With Command Prompt Restore
During instances where the computer user can not access Windows desktop and the computer has become infected with malware, viruses, or other conflicts and malfunctions, entering Windows utilizing sage mode with command prompt is the suggested step to access Window’s restore center. If it is difficult to start windows in safe mode or if Windows’s brings up a black screen, with “safe mode” in the four corners – Don’t panic. Move your cursor to the lower left corner, where the Search box is usually visible in Windows Start Menu and it will come up, including the “Run” box.
1. Restart/reboot your computer. Unplug if necessary.
2. Enter Windows in “safe mode with command prompt”. To properly enter safe mode, repeatedly press F8 upon the opening of the boot menu.
3. Once the Command Prompt appears type “explorer” and hit Enter. Sometimes during infections of malware and viruses you only have the opportunity to do this within 2-3 seconds. In some cases if this is not performed during the allotted seconds, viruses such as the FBI MoneyPak ransomware virus will not allow you to type “explorer” anymore.
4. Once Windows Explorer shows up browse to:
- Win XP: C:\windows\system32\restore\rstrui.exe and press Enter
- Win Vista/Seven: C:\windows\system32\rstrui.exe and press Enter
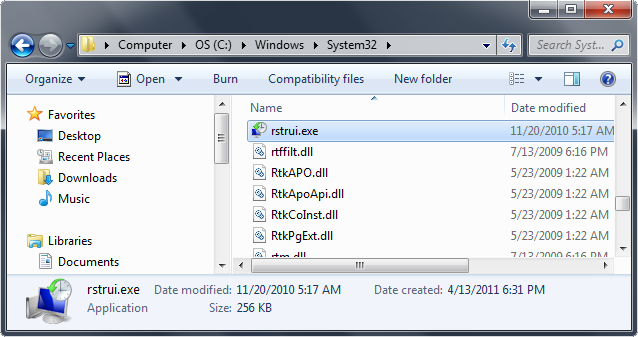
5. Follow all steps to restore or recover your computer system to an earlier time and date, before infection to complete Windows restore.









Thanks so much for all the info. I got this message while at a friends house and didn’t know what to think. You made my week.
Glad you were able to get rid of it!
Thanks for the motivating words.
i was told possibly this virus can encrypt files also…how would i know if that has happened? thanks for all the info…very helpful.
If you would like to locate encrypted files on your computer please visit this link for more instructions: http://social.technet.microsoft.com/Forums/windows/en-US/7dfe0ee1-3de8-46f1-bdbb-3e5ec23ffa18/backup-encryption-key-prompt
Thank you so much for the info…really help ke out!!! 🙂