New vulnerabilities in Oracle’s Java Runtime Environment (JRE) have been discovered that target the newest version of JRE (1.7) and allow cyber criminals to exploit computer systems and internet browsers via Runtime products such as Oracle’s Java plugin (Java Deployment Toolkit, etc.) for popular internet browsers.

The Java vulnerability allows hackers to exploit Internet Explorer, Firefox, Opera, Google Chrome and also Safari on multiple platforms including Windows, Linux and MacOS.
Java Exploit Dangers
A Java exploit can introduce a computer system to malware, viruses, and Trojans giving attackers complete access to the infected computer system. If the Java exploit is not fixed, your computer may lose functionality and you are at a very high risk of becoming a victim to cyber crime involving credit theft, exploitation schemes, identity theft, and more.
Java Exploit Kits
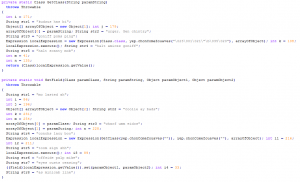 Cyber criminals utilize a variety of exploits to affect Java users, the most popular being the Blackhole exploit kit. The Blackhole exploit kit is currently the most prevalent web threat to date, whose purpose is to deliver a malicious payload to a victim’s computer.
Cyber criminals utilize a variety of exploits to affect Java users, the most popular being the Blackhole exploit kit. The Blackhole exploit kit is currently the most prevalent web threat to date, whose purpose is to deliver a malicious payload to a victim’s computer.
Another exploit kit is the Nuclear Pack exploit kit and both mentioned packs use the same principle and serve two latest Java vulnerabilities (CVE-2012-1723 and CVE-2012-4681) together inside one single jar file. This allows attackers to attack all environments (up to JRE 1.6 and JRE 1.7) with just one applet tag included inside the landing page of the proposed exploit kit.
Java Exploitation Process
- Cyber criminals license the Blackhole exploit kit from it’s authors and specifies various options to customize the kit, including a landing page on the internet.
- A victim loads a compromised web page or opens a malicious spam link.
- The compromised web page or malicious link sends the user to the Blackhole exploit kit server’s landing page.
- This landing page contains obfuscated Java that loads all exploits to the computer and possibly a Java applet tag that loads a Java Trojan horse.
- The exploit loads and executes a payload on the victim’s computer and informs the Blackhole exploit kit server as to which exploit was use to load the payload.
How To Fix The Java Exploit – Protection Against Attack
There are several options to assess Java vulnerabilities and remove payloads of malware that have infected your computer system, but disabling Java is the most recommended solution to bypass any sort of Java attack.
Update Java – JDK 8 (with JavaFX) Early Access for ARM
Oracle has apparently repaired the issue with an early release of JDK 8, including JavaFX. Click a link below to update Java or visit http://www.oracle.com/technetwork/java/javase/downloads/index.html for more download information.
Java Platform (JDK) 7u10 |
JDK 7u10 + NetBeans |
Please note, Java is needed for some websites and clients to operate properly.
How To Disable Java – Disable/Remove/Uninstall Java Plugin Instructions
The instructions below detail how to disable or remove the Java plugin from Windows, Mac OS, and popular internet browsers.
Windows:
Navigate to Start > Control Panel, click the Uninstall a program or Add and remove programs. Find Java on the list of programs. If you have version 6 or 7, uninstall it.

Mac OS X 10.7 and 10.8:
Navigate to Macintosh HD > Library > Java > JavaVirtualMachines > and remove the 1.7.0.jdk file. Older versions of OS X run Java 6.
Mozilla Firefox:
From the main menu select Tools > Add-ons. In the Add-on management window, choose Plugins. Find any plugins on the list that say Java and click the Disable button. Restart Firefox (Java Runtime, Java Deployment Toolkit).

Google Chrome:
Click the customize icon (3 bar or wrench) and navigate to Tools > Extensions. Search for any plugins on the list that say Java and click the Disable button.
Disable Java Plugin (Chrome)
Open Preferences and type Java in the search box (or type chrome://plugins/ into the browser address bar). Scroll down to the Plug-ins section, and click the Disable individual plug-ins link. If you have Java installed, you should see a “disable” link underneath the Java Plugin listing.
Internet Explorer:
Disabling Java in IE is complicated. To learn how to disable the Java web plug-in in Internet Explorer please visit: http://support.microsoft.com/kb/2751647
Change Java Registry In Windows (IE)
1. Open Windows Start Menu and type regedit in the search box, press Enter.
2. Change the HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft\Java Plug-in\\UseJava2IExplorer registry value to 0, where is any version of Java on your system. For example,
if you are running a 32-bit version of Java on a 64-bit platform, you should set the HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\JavaSoft\Java Plug-in\\UseJava2IExplorer registry value to 0.
3. Run javacpl.exe as administrator, click the “Advanced” tab, select “Microsoft Internet Explorer” in the “Default Java for browsers” section, and press the space bar to uncheck it. This properly sets the above registry value, despite the option being grayed out.
Safari:
Click Preferences > Security tab > uncheck the Enable Java option.
Opera:
Type opera:plugins into the browser’s address bar. Find any plugins on the list that say Java and click the Disable button.
Real-Time Protection
The malware that is being spread by the exploit is currently detected by Malwarebytes Anti-Malware, if you have the Pro version, you will be actively protected from the threats by either having the IP of the malicious exploit site blocked or the malware itself will be unable to run.
Detect And Remove Malware, Viruses, And Trojans
If you suspect your computer has been infected with malware, viruses, and/or Trojan horses due to a Java exploit, or Java attack it is recommended to use a reputable Antivirus or Anti-Malware software.
Software links provided will always lead to the lowest discounted prices on the internet.
| Antivirus Software (MAC) | Purchase | Free Downloads |
|---|---|---|
| ESET |
Buy ESET Antivirus |
30 Day Trial |
| McAfee | Buy McAfee Antivirus | View All Products |
| MacPaw |
Buy MacPaw Cleaner Mac |
|
| MacKeeper |
Buy MacKeeper: 911 |








Thanks! I decided to disable Java, i don’t know if I use it or not but have not noticed anything weird.
The New Year could not have started off with a bigger malware outbreak than this Zero-Day Java exploit. Millions of computers worldwide are at risk of getting infected by simply browsing the web. In this post we will share with you the technical details behind this attack and give you tips on how to protect yourself.
Direct from our researchers: Malware is spreading through new Java exploit. Read more on our blog and make sure you have Malwarebytes PRO to stay protected!